Method and device for controlling policy
A technology for policy control and header loading, applied in the field of communications, can solve the problems of inability to control user services and network resources, not giving, and unable to obtain the applicable scope of policy control related information, so as to improve the utilization of network resources and ensure service experience. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
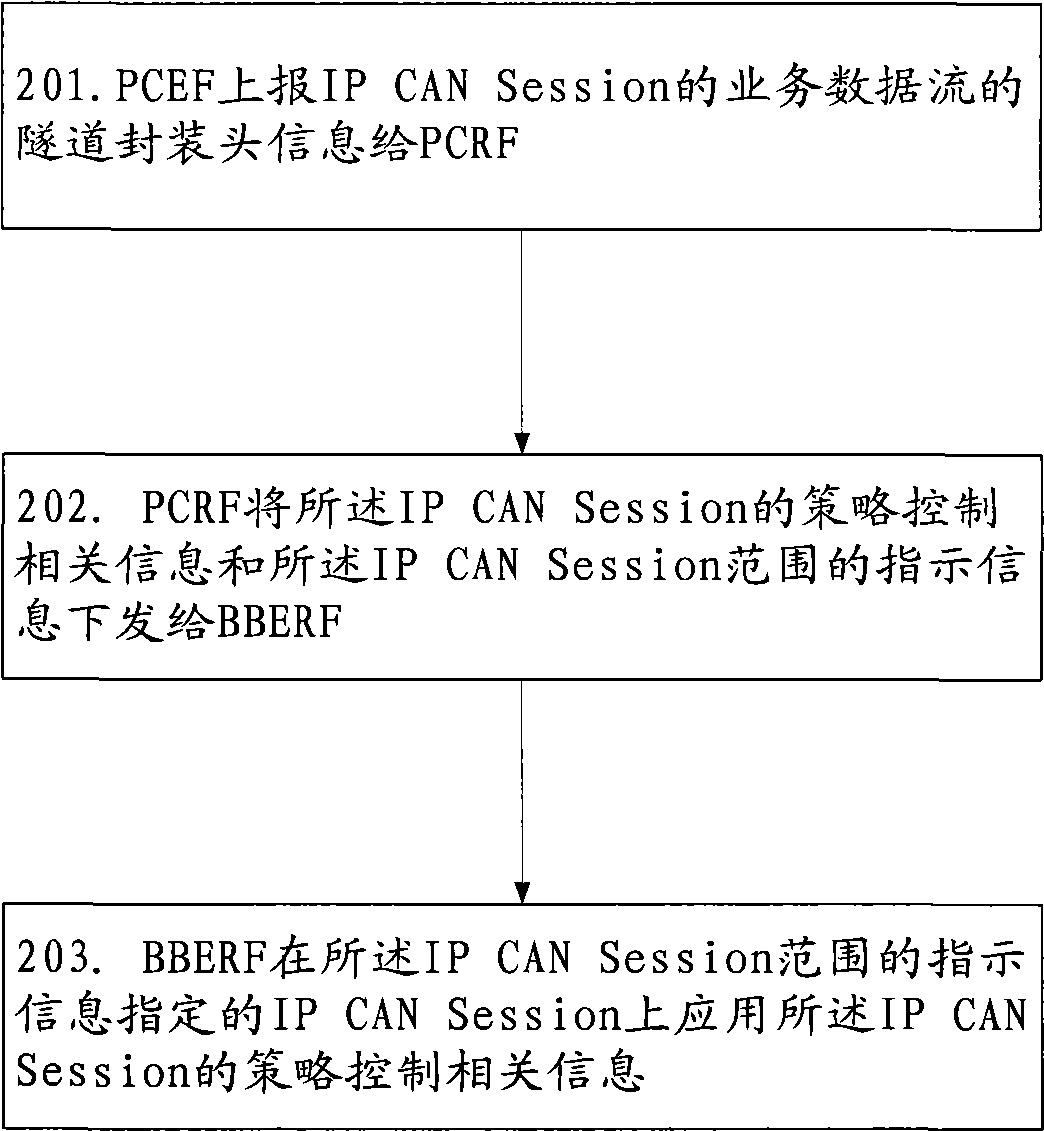
[0069] The method in Embodiment 2 realizes: when the UE establishes an IP CAN Session to a certain PDN, the PCEF initiates the establishment of the IP CAN Session and its corresponding Gx session to the PCRF, and carries a tunnel in the GRE encapsulation format of the service data flow of the IP CANSession Encapsulation header, PCRF uses the GRE-Key in the tunnel encapsulation header as the indication information of the IP CAN Session range, sends the GRE-Key and the uplink AMBR of the IPCAN Session to BBERF, and BBERF applies the uplink AMBR to the corresponding IP CAN Uplink non-GBR service data flow in the session range.
[0070] Such as Figure 4 as shown, Figure 4 A schematic flowchart of the method for specifying the scope of application of policy control-related information in Embodiment 3 of the present invention is given.
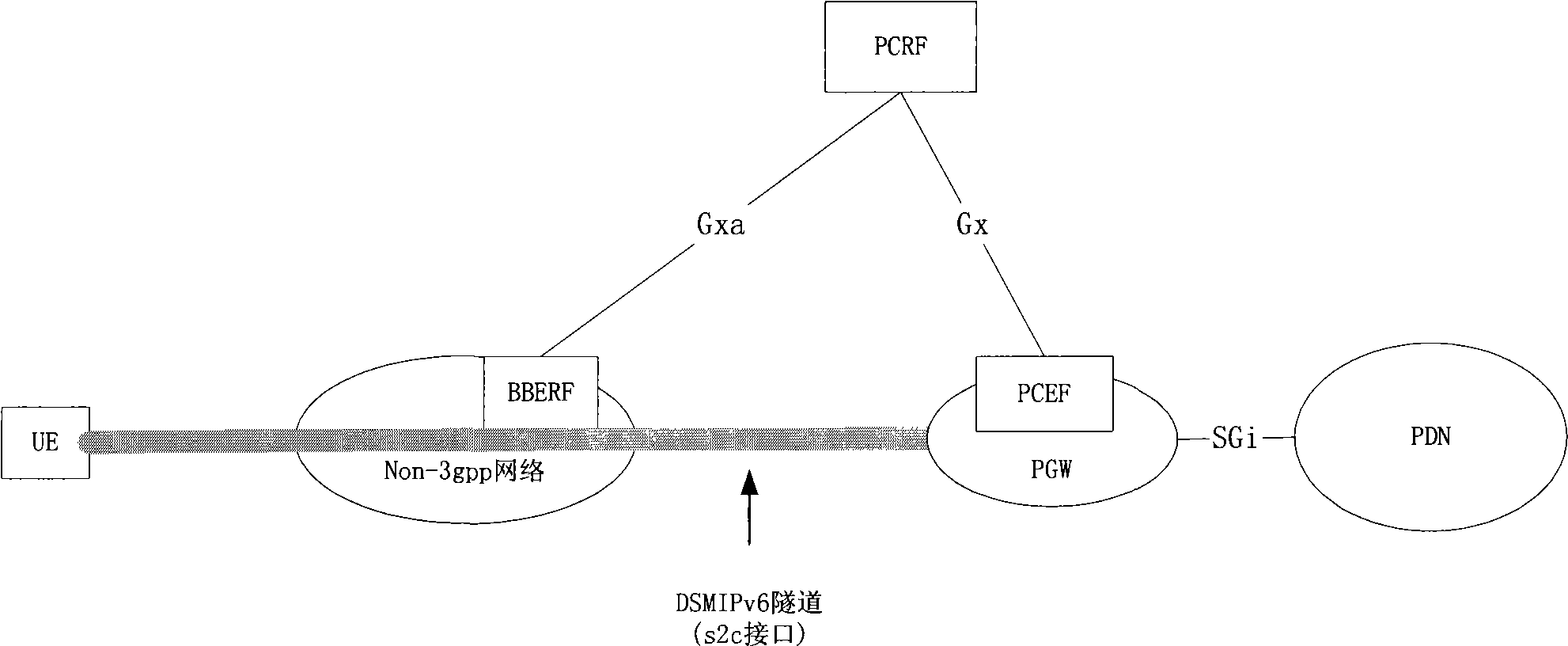
[0071] In step 401, the UE is attached to the non-3gpp network, the non-3gpp network allocates a CoA for the UE, and a corresponding Gx...
Embodiment 3
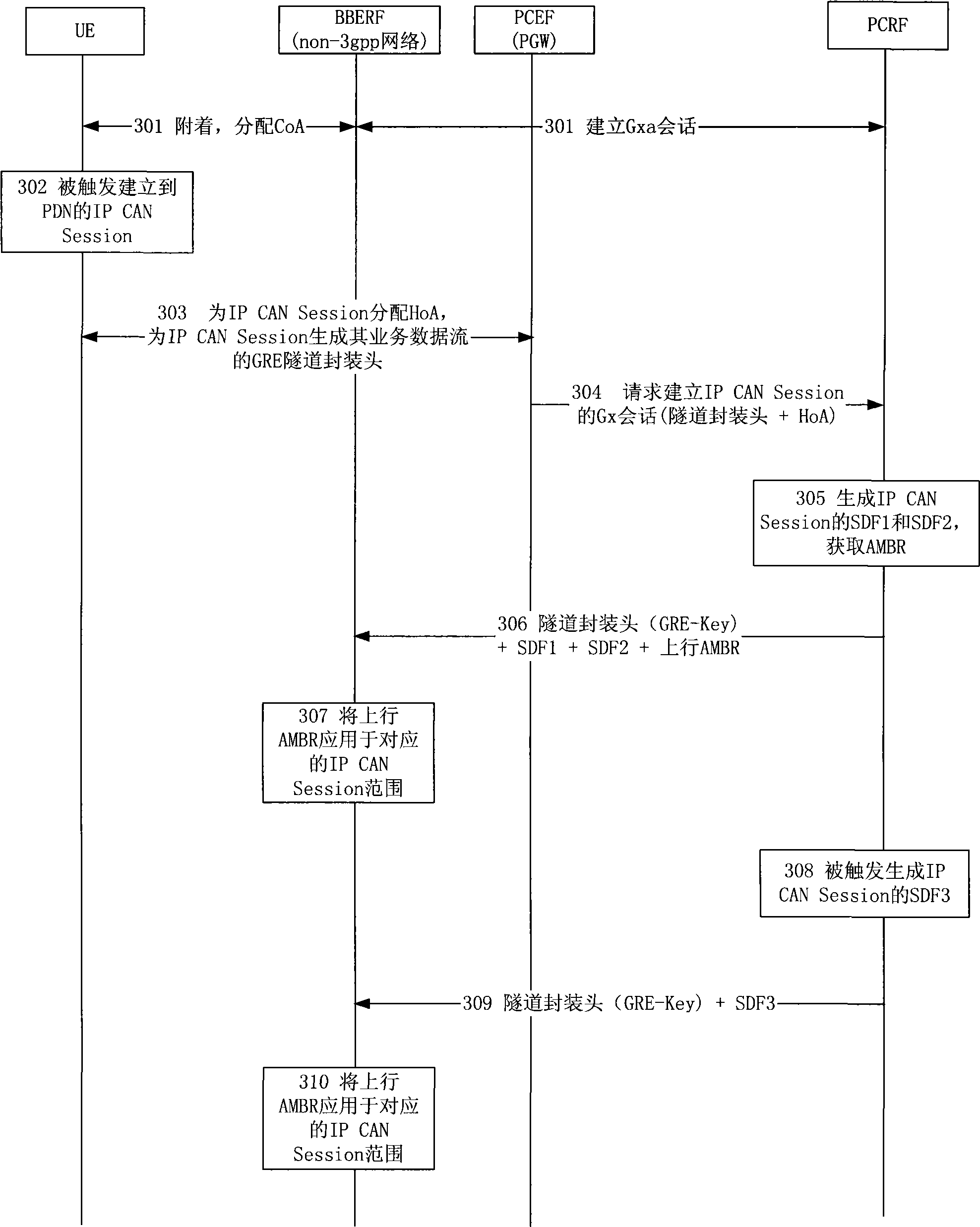
[0080] The method of Embodiment 3 realizes: when the UE establishes an IP CAN Session to a certain PDN, the PCEF initiates the establishment of the IP CAN Session and its corresponding Gx session to the PCRF, and carries a tunnel in the GRE encapsulation format of the service data flow of the IP CANSession Encapsulation header, PCRF uses the combination of GRE-Key, CoA, tunnel PGW end address, and upper layer protocol type (GRE) in the tunnel encapsulation header as the indication information of the IP CAN Session range, and successively the indication information and the The uplink AMBR of the IP CANSession is delivered to the BBERF, and the BBERF applies the uplink AMBR to the uplink non-GBR service data flow within the scope of the corresponding IPCAN Session.
[0081] Such as Figure 5 as shown, Figure 5 A schematic flowchart of a method for specifying the scope of application of policy control-related information in Embodiment 4 of the present invention is given. ...
Embodiment 4
[0091] The method of Embodiment 4 realizes: when the UE establishes an IP CAN Session to a certain PDN, the PCEF initiates the establishment of the IP CAN Session and its corresponding Gx session to the PCRF, and carries a tunnel in the GRE encapsulation format of the service data flow of the IP CANSession The encapsulation header, PCRF generates the indication information of the IP CAN Session range of the IP CAN Session according to the GRE-Key in the tunnel encapsulation header, and successively reports and subscribes the indication information and the events of the IP CAN Session to BBERF, BBERF Apply the event reporting subscription to the corresponding IP CAN Session scope.
[0092] Such as Figure 6 as shown, Figure 6 A schematic structural diagram of a device for specifying the scope of application of policy control-related information in Embodiment 5 of the present invention is given.
[0093] A device for specifying the scope of application of policy contr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com