Method and network appliance for preventing IPv6 packet attack
A network equipment and packet technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems of low accuracy, inability to distinguish attack packets and non-attack packets in detail, and achieve the goal of improving accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
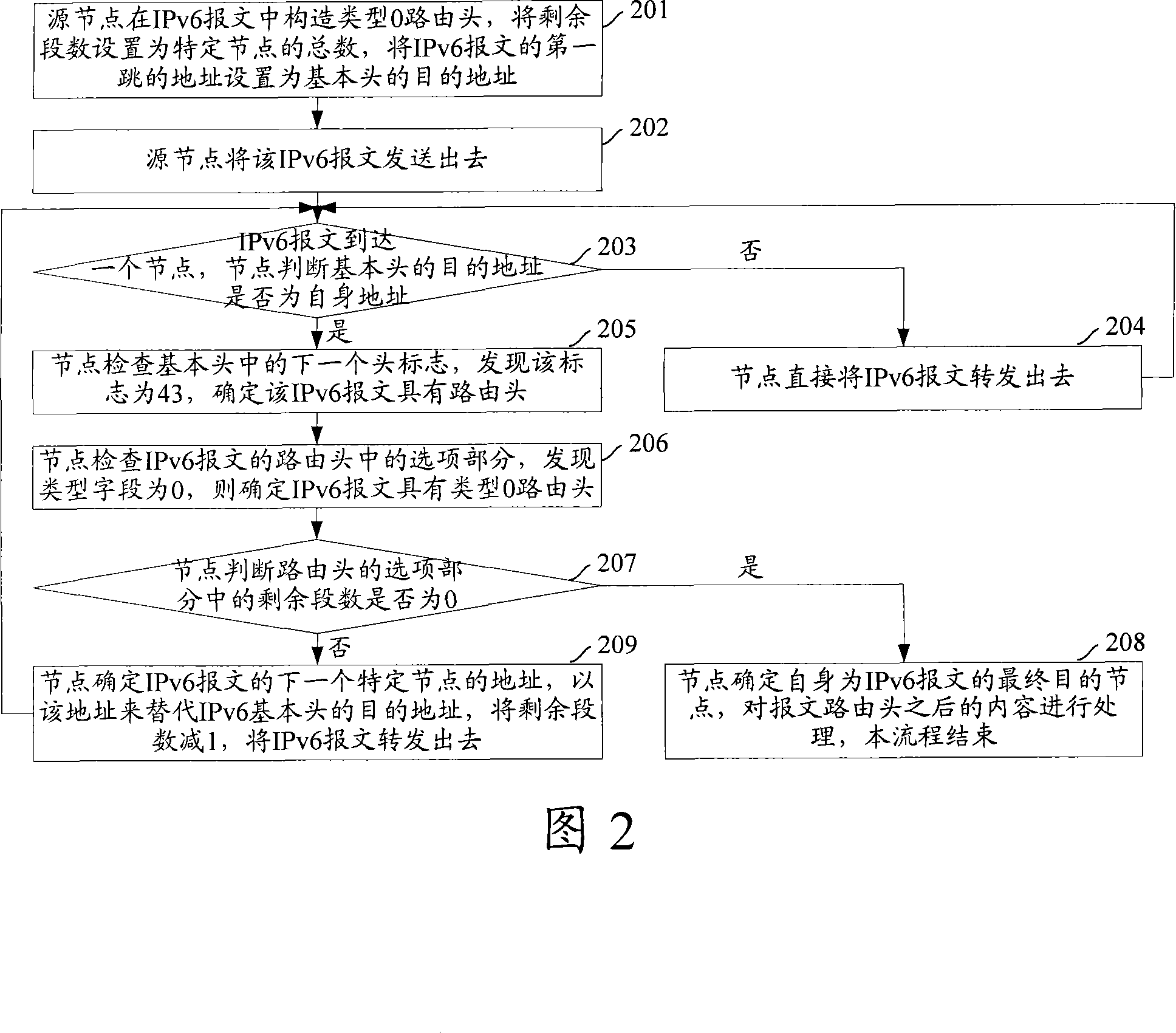
[0045] Fig. 4 is the flow chart that prevents IPv6 report attack that the embodiment of the present invention provides, as shown in Fig. 4, its specific steps are as follows:
[0046] Step 401: the source node constructs a type 0 routing header in the IPv6 message, which includes the address of the specific node that the message needs to pass through to reach the final destination node, sets the remaining segment number as the total number of the specific node, and sets the IPv6 message's The address of the first hop is set to the destination address of the basic header.
[0047] Step 402: the source node sends out the IPv6 message.
[0048] Step 403: When the IPv6 packet arrives at a node, the node judges whether the destination address of the basic header is its own address, and if so, executes step 405; otherwise, executes step 40...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com