Key control method and apparatus, and terminal
A control method and key technology, applied in the field of communications, can solve problems such as poor user experience and misoperation, and achieve the effect of improving user experience and avoiding misoperation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
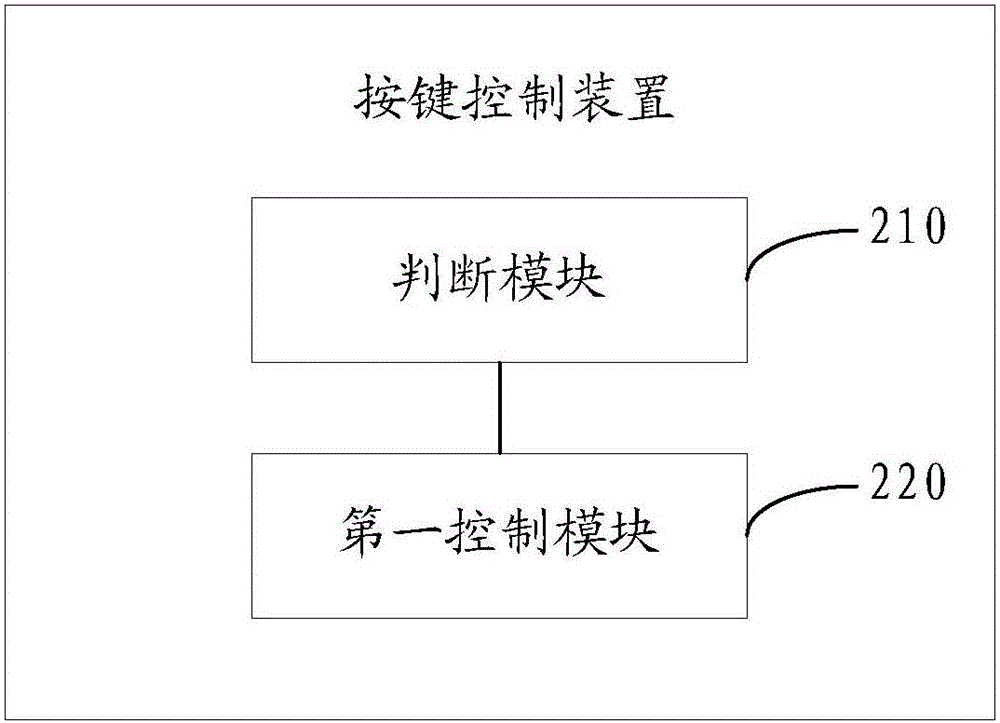
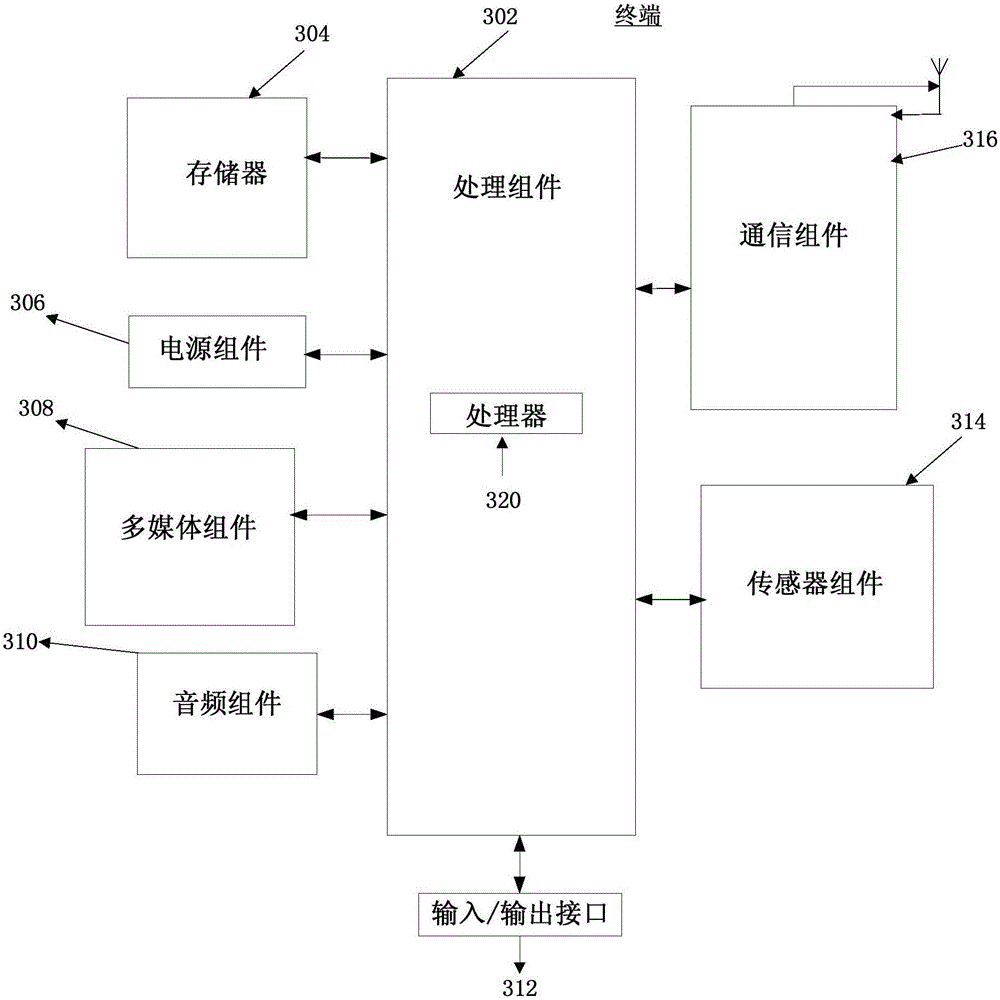
[0064] An embodiment of the present invention provides a button control method, which can be applied to terminals such as mobile phones and tablet computers. The information processing method can be realized through an application program, and the application program can be installed on terminals such as mobile phones and tablet computers.
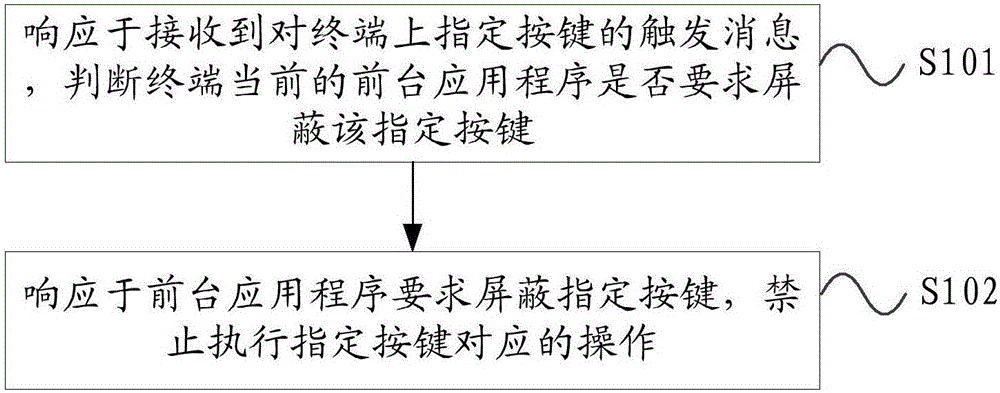
[0065] figure 1 It is an example flow diagram of the button control method provided by the embodiment of the present invention. The process of the button control method is applied to a terminal. Such as figure 1 As shown, in this embodiment, the button control method may include the following steps:
[0066] S101. In response to receiving a trigger message for a specified key on the terminal, determine whether the current foreground application of the terminal requires shielding the specified key;
[0067] S102. In response to the request of the foreground application program to shield the specified key, prohibit execution of the opera...
example 1
[0080] The user adds the UID corresponding to the application of game A on the mobile phone to the set of blocked applications corresponding to the return key.
[0081] When the user opens the application of game A to play the game, he accidentally touches the return key. At this time, the mobile phone obtains the UID corresponding to the application of game A and the shielded application set corresponding to the return key, and then judges according to the obtained information. When the mobile phone determines that the UID corresponding to the application of game A is in the shielded application set corresponding to the return key , the return operation corresponding to the return key is prohibited, thereby preventing the mobile phone from exiting the application program interface of game A.
example 2
[0083] The user adds the UID corresponding to the Alipay application on the mobile phone to the set of blocked applications corresponding to the HOME key.
[0084] When the user opened the Alipay app to transfer money, he accidentally touched the HOME button. At this time, the mobile phone obtains the UID corresponding to the Alipay application and the shielded application set corresponding to the HOME key, and then judges based on the obtained information. When the mobile phone determines that the UID corresponding to the Alipay application is in the shielded application set corresponding to the HOME key, It is forbidden to perform the operation corresponding to the HOME key to return to the main desktop of the mobile phone, thereby preventing the mobile phone from exiting from the Alipay application interface. In this way, the unsafe exit of Alipay is prevented, and the user can only exit safely through the Alipay interface, thereby protecting the security of the user accoun...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com