Method for selecting optimized protection strategy for network security
A protection strategy and network security technology, applied in the field of network security, can solve the problems of not considering the implementation cost, high cost of test bed, lack of accuracy of simulation results, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
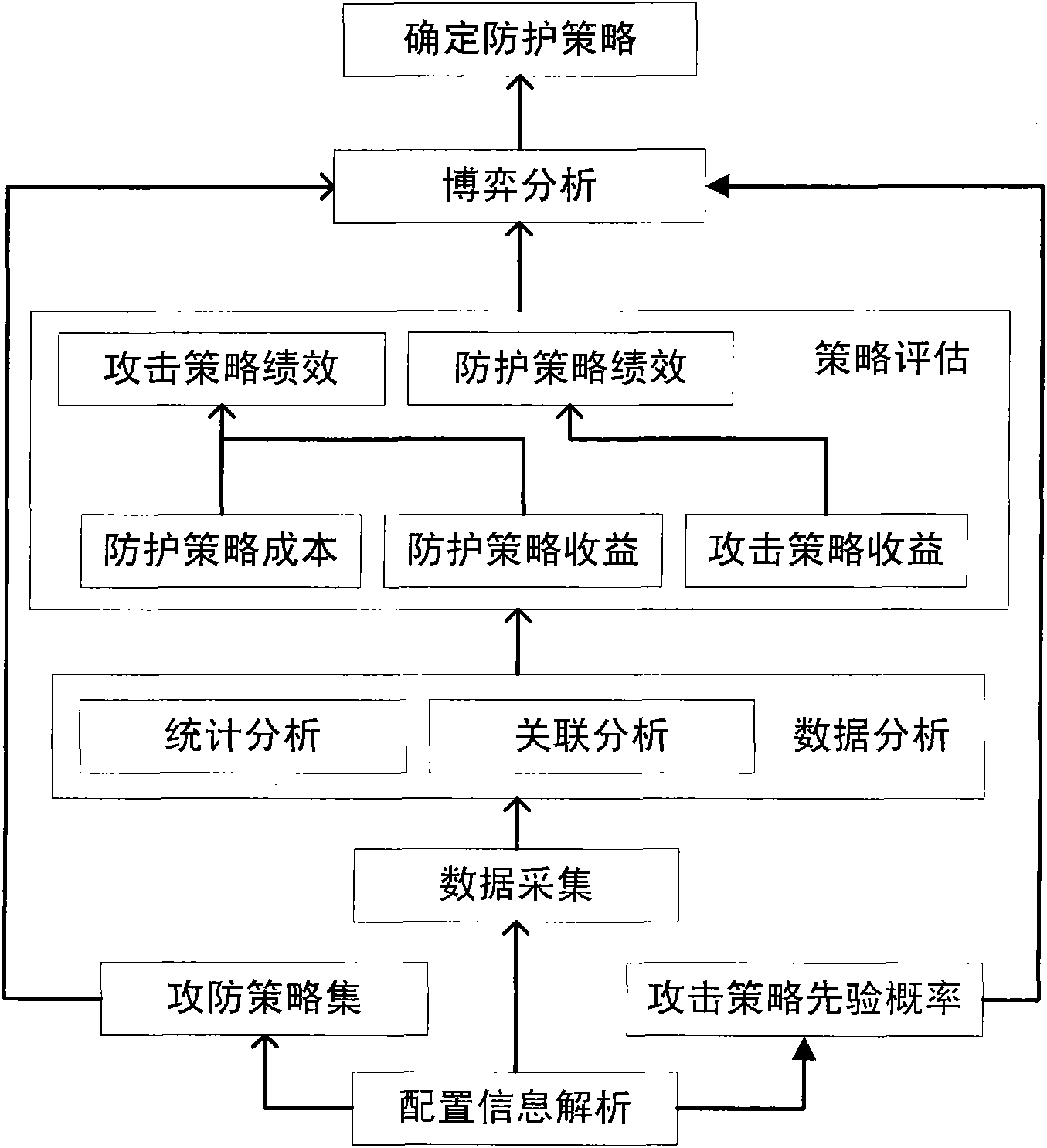
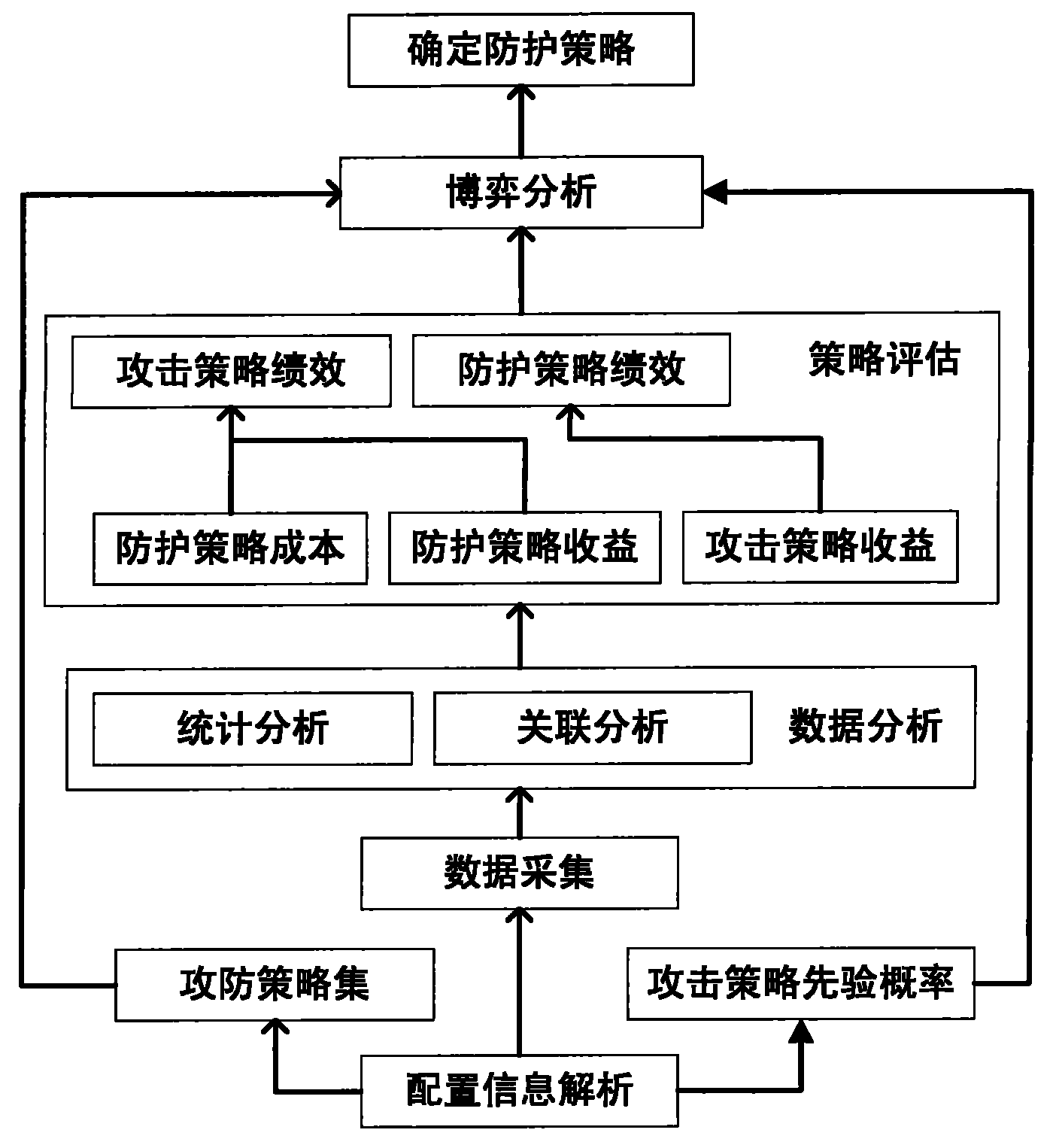
[0032] First, analyze user configuration information as a guide for performance evaluation; secondly, collect host information, link information, service information, protection system information, economic cost information and asset importance information in the process of attack and defense; then normalize the format Statistical analysis and correlation analysis are carried out on the information, and then the performance of the offensive and defensive strategies is calculated using the analyzed information; finally, the game analyzes the offensive and defensive strategy sets and gives suggestions for the selection of defensive strategies.
[0033] Referring to the accompanying drawings, the detailed process is given below.
[0034] Step 1: Use the configuration information parsing module to parse user configuration information
[0035] The user configuration information refers to the performance evaluation configuration information input or formulated by the user, and the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com