Detecting system for suspect DBMS intrusion and detecting method thereof
An intrusion detection system and malicious intrusion technology, applied in transmission systems, digital transmission systems, special data processing applications, etc., can solve problems such as multiple deletions and complex countermeasures, and achieve the effect of preventing malicious codes from being stolen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0051] The present invention will be described in detail below with reference to the accompanying drawings.
[0052] The invention is an untrusted DBMS malicious intrusion detection system and method.
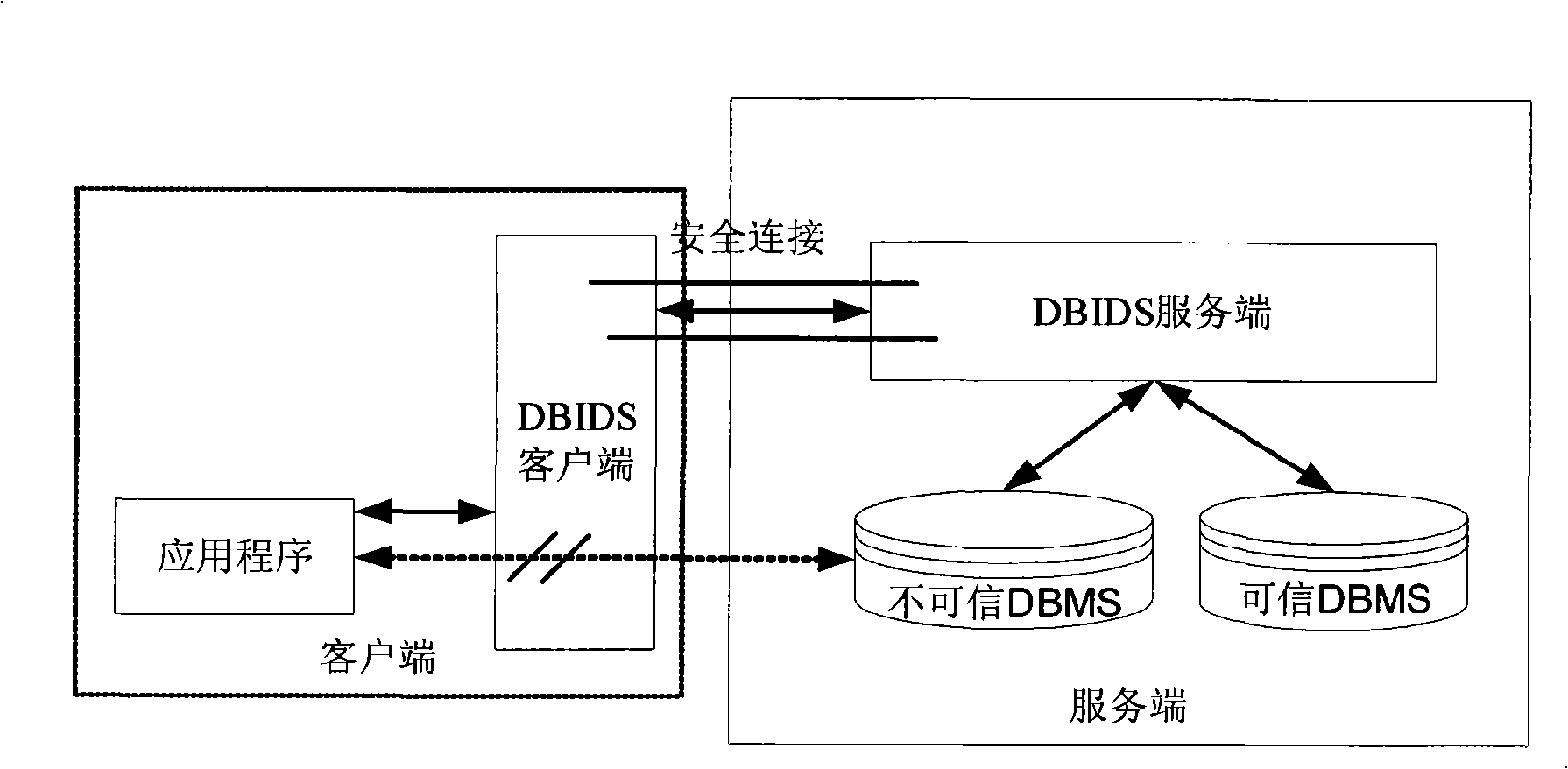
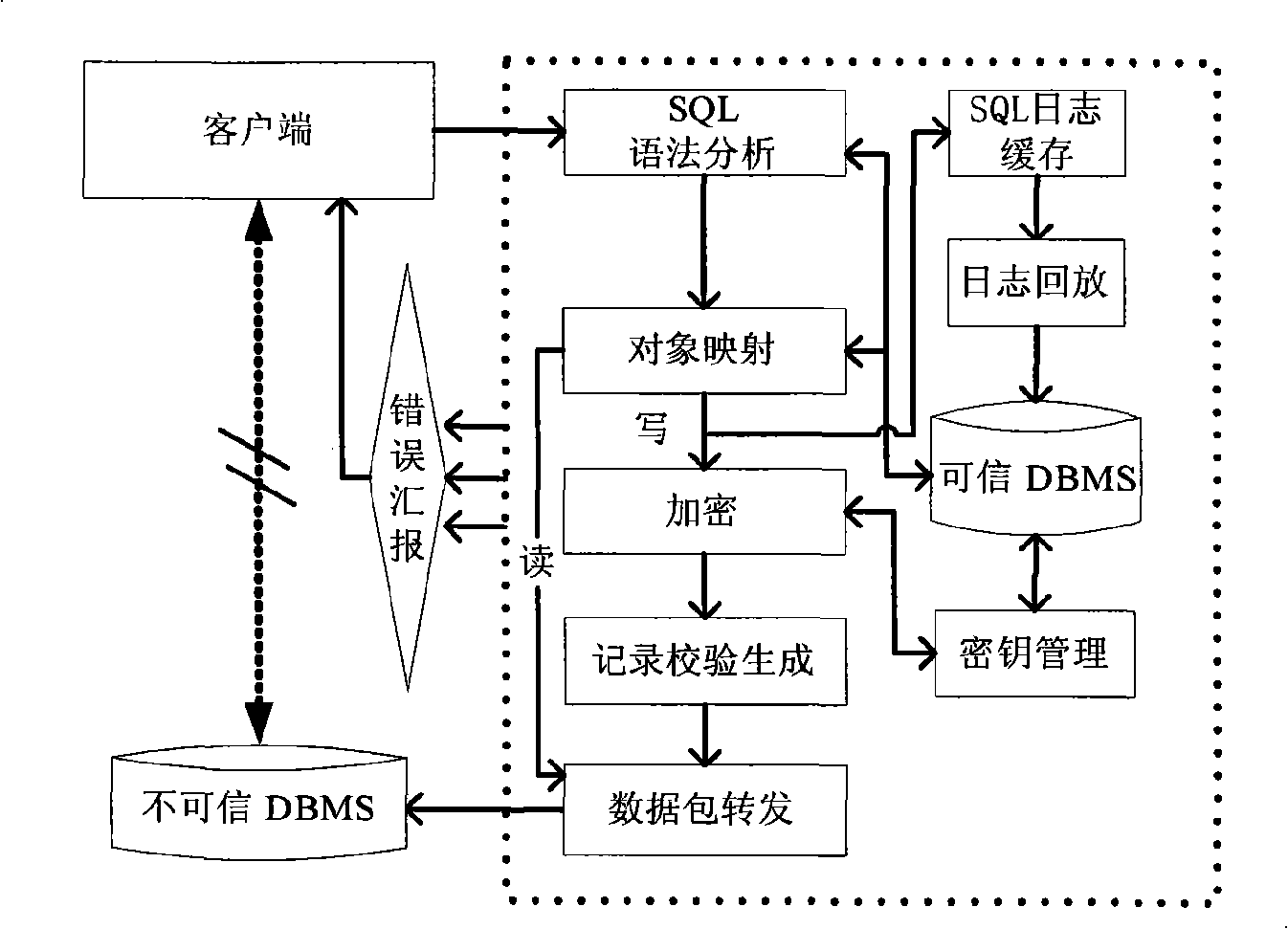
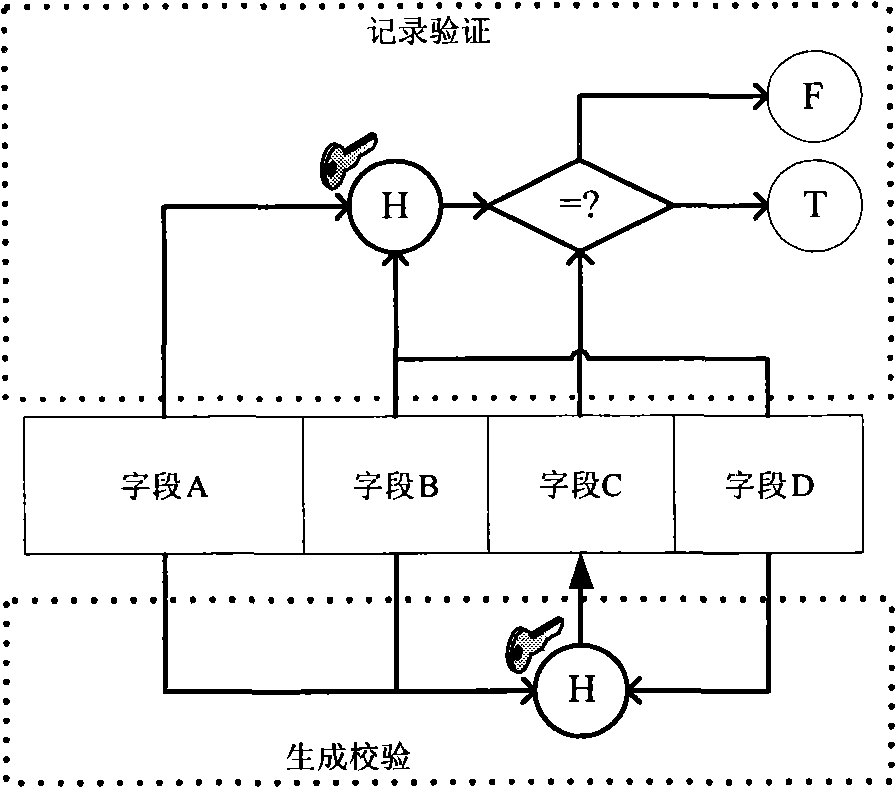
[0053] Such as figure 1 In the present invention, a database intrusion detection system (DBIDS) is introduced between the DBMS and the database application to intercept the message communication between the DBMS and the application, so as to detect malicious behaviors and protect key data. DBIDS is divided into two parts: client and server. The client is mainly responsible for database message interception and forwarding, and the server is responsible for client identity authentication, analysis of communication protocols, transparent data encryption and decryption, and malicious database intrusion detection functions.
[0054] DBIDS uses data forwarding to intercept database communications. When setting the server address on the database client, use the address and port of the DB...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com