An automatic authorization method for access control based on face recognition
An automatic authorization and face recognition technology, applied in the multimedia field, can solve the problems of easy to be stolen by others, easy to lose the radio frequency card, can not absolutely guarantee the safety of the home, etc. Improved accuracy and timeliness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
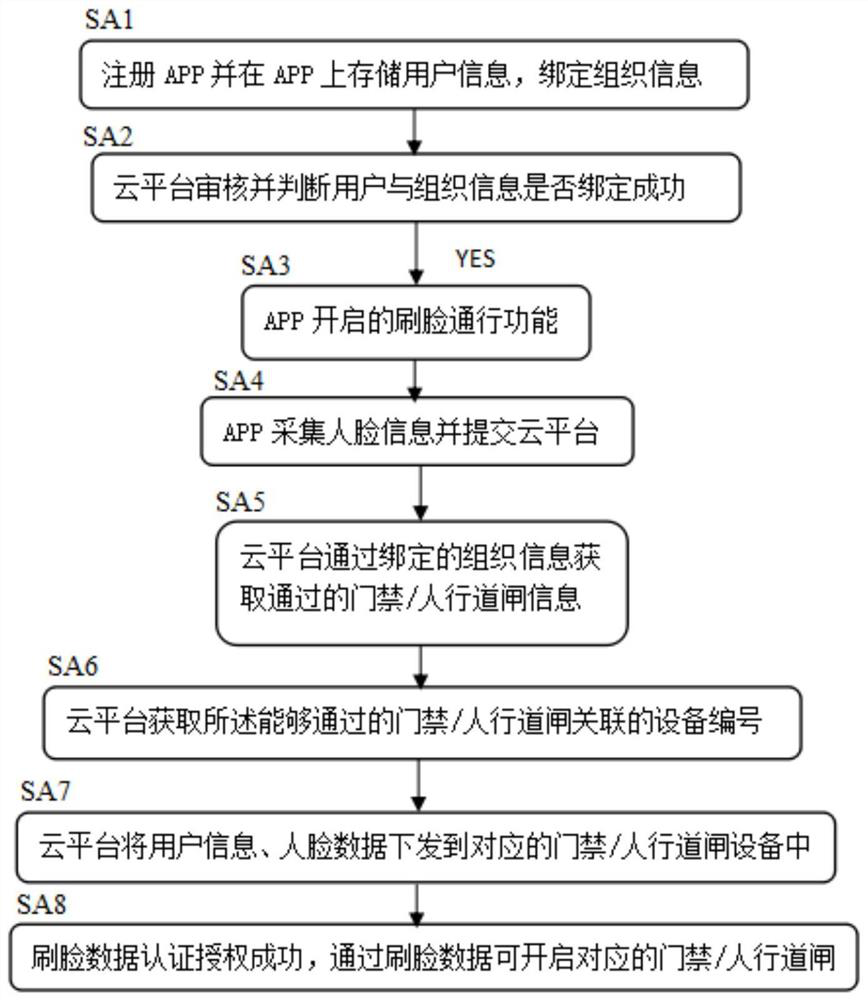
[0032] This embodiment provides a method for automatic authorization of access control based on face recognition, such as figure 1 shown, including steps:
[0033] SA1. Register APP and store user information on APP, and bind organization information;
[0034] SA2, the cloud platform reviews and judges whether the binding of user and organization information is successful, if so, skip to step SA3;
[0035] SA3, the face-scanning pass function enabled by the APP;
[0036] SA4, the APP collects face information and submits it to the cloud platform;
[0037] SA5. The cloud platform obtains the information of the access control / sidewalk gate through the bound organization information;
[0038] SA6. The cloud platform obtains the device number associated with the passable access control / sidewalk gate;
[0039] SA7, the cloud platform sends the user information and face data to the corresponding access control / sidewalk gate device;
[0040] SA8. The authentication and authoriza...
Embodiment 2
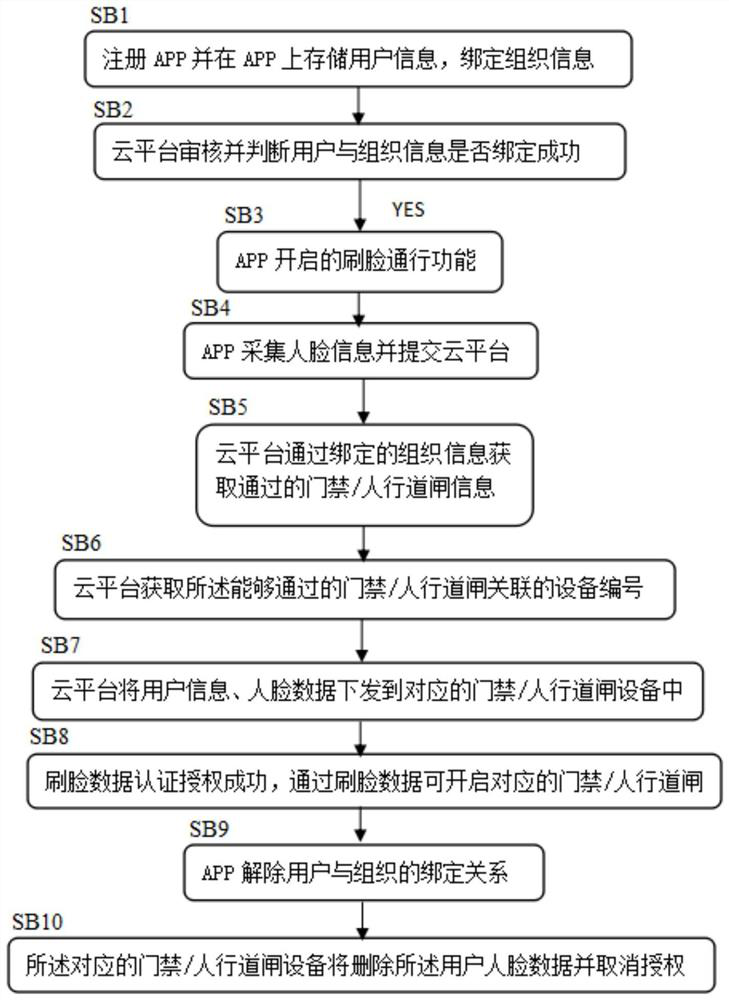
[0052] This embodiment provides a method for automatic authorization of access control based on face recognition, such as figure 2 shown, including steps:
[0053] SB1. Register APP and store user information on APP, and bind organization information;
[0054] SB2. The cloud platform reviews and judges whether the binding of the user and organization information is successful, and if so, skips to step SB3;
[0055] SB3, the face-scanning pass function enabled by the APP;
[0056] SB4, the APP collects face information and submits it to the cloud platform;
[0057] SB5. The cloud platform obtains the information of the access control / sidewalk gate through the bound organization information;
[0058] SB6. The cloud platform obtains the device number associated with the passable access control / sidewalk gate;
[0059] SB7, the cloud platform sends the user information and face data to the corresponding access control / sidewalk gate device;
[0060] SB8. The face-swiping data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com