A method of security control flow execution
A security control and process technology, applied in the field of computer programs, can solve problems such as insufficient security of multi-stage request processes, and achieve high security, easy expansion, and simple effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
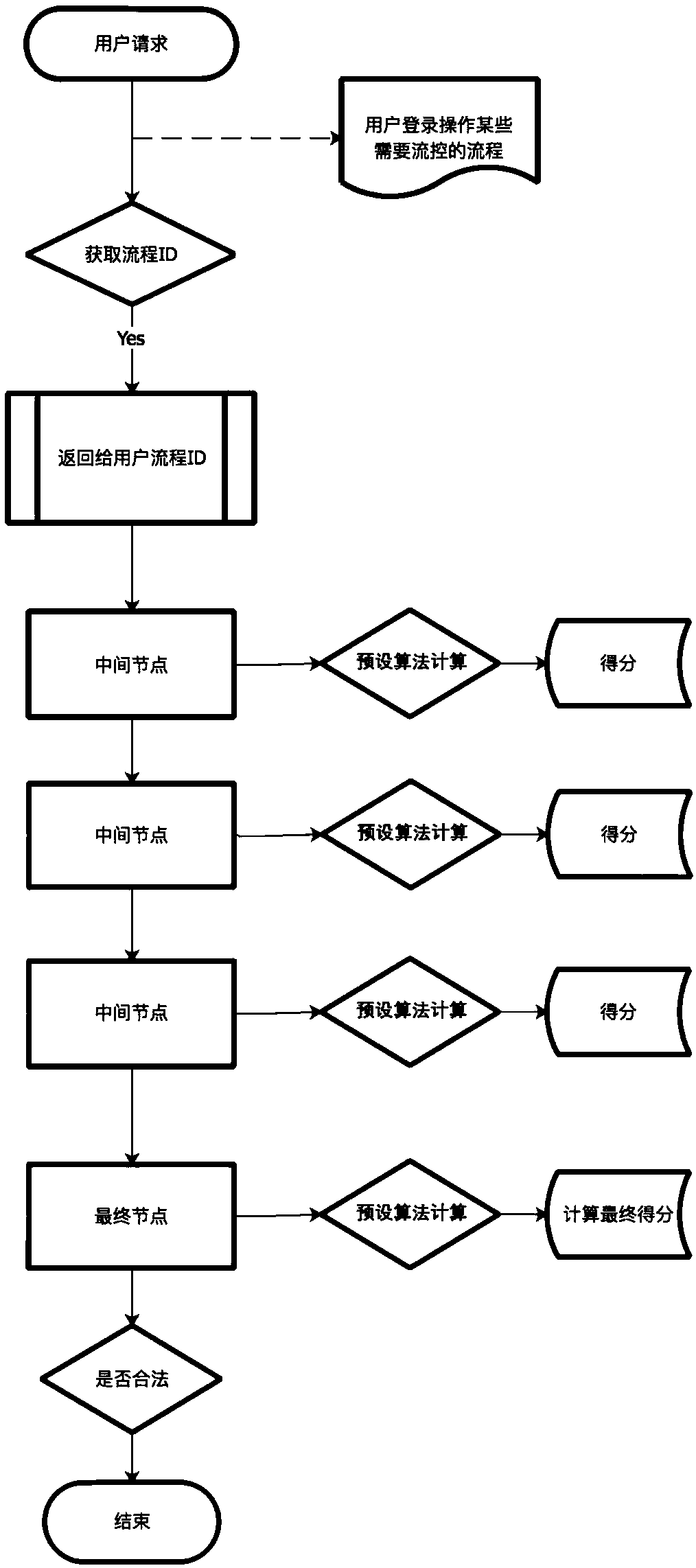
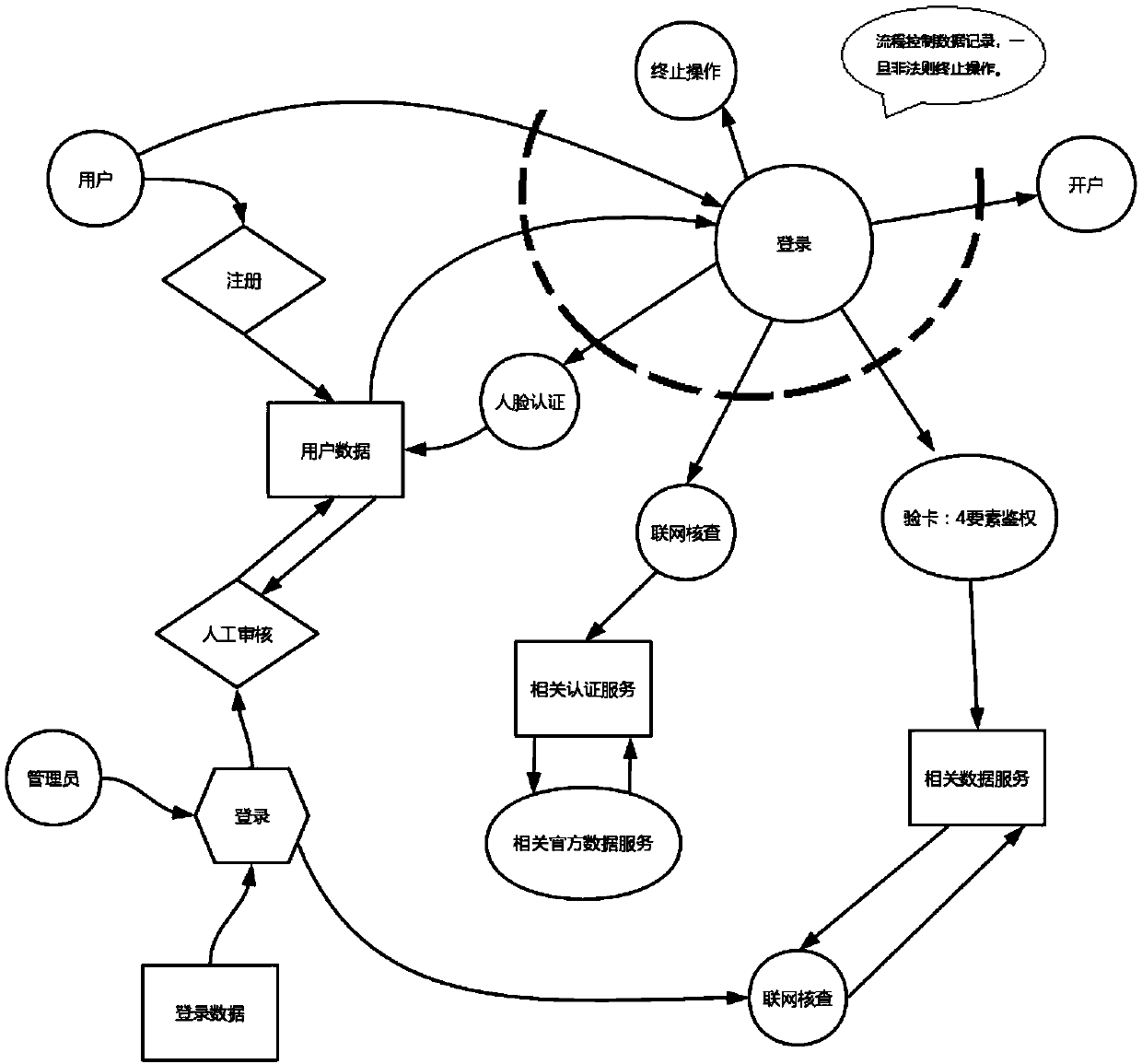
[0037] Such as image 3 As shown, this embodiment is an example process of simulating account opening. Account opening is the last node, and the pre-intermediate nodes include requesting face, identity verification, card verification, and SMS verification. only process nodes.
[0038] Since the request involves many services, the process is also decomposed into multiple stages in the functional design, resulting in the fact that one request cannot complete the business operation. It needs to interact with the background multiple times and record the corresponding status data in the background before it can be truly implemented. effective interaction. However, the whole process is very long, and if a potential illegal user wants to tamper with the request operation to illegally open an account, it may have immeasurable consequences.
[0039] The entire process is pre-defined, not only a certain operation, but even multiple processes will also be considered illegal requests, b...
Embodiment 2
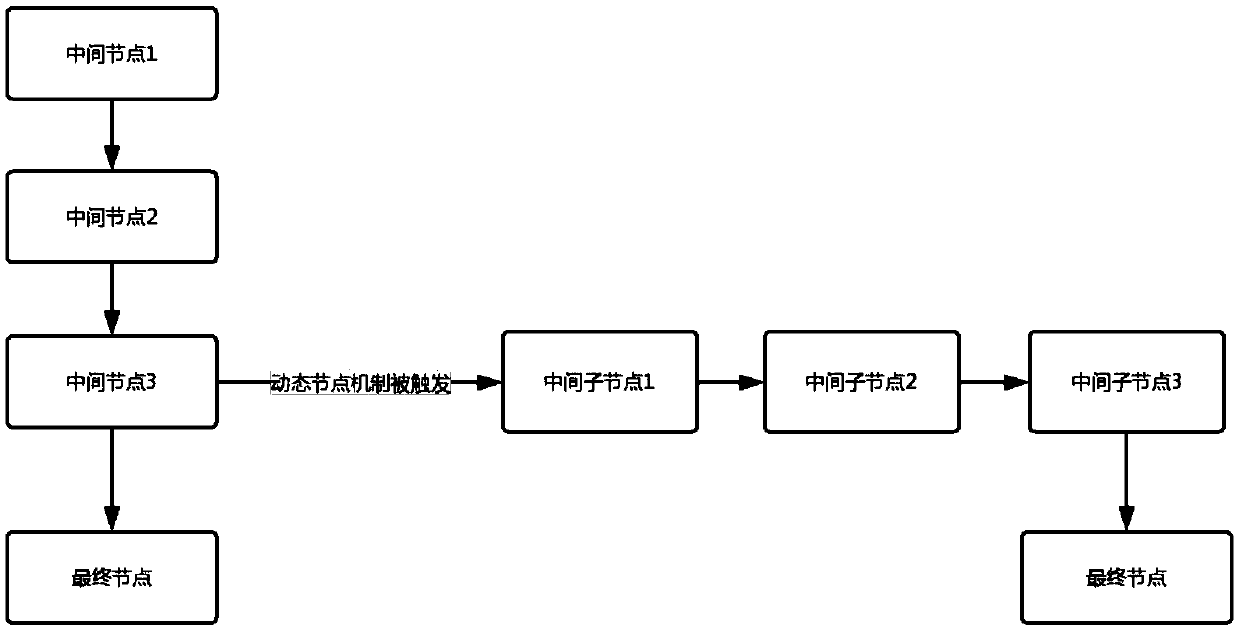
[0047] When a process node contains a dynamic node, once the dynamic node is triggered, the preset score will change. Taking the process of transferring money to an unbound card as an example, there are several ways to transfer out to an unbound card. Here, the fingerprint payment process is used to illustrate. The process includes: fingerprint (11 points)->SMS (7 points)- >Face (3 points)[Dynamic]->Transfer without binding card, in which 'face' is a dynamic node in this process, if the user's single transfer amount exceeds the preset amount, the 'face' node will be triggered , the preset score for the whole process is 231. If the user's single transfer amount does not exceed the preset amount, the face node will not be triggered, and the preset score is 77 points.
[0048] If the user transfers out of the non-bound card in a single transaction and exceeds the limit of a single preset amount, the new preset score will be recalculated to become 231 points. On the contrary, it ...
Embodiment 3
[0051] Step 1: Define a preset database table for recording process control request records, which mainly includes: process name, preset score, process number, status, actual score, etc.
[0052] Step 2: Sort out the process of existing multi-stage scenarios, and pre-define each scenario, including specific intermediate nodes and final nodes, and define their process names. (either file configuration or database storage)
[0053] Step 3: Define each specific process node in the process, and define a name and a score for the node, where the score must be a prime number. (either file configuration or database storage)
[0054] Step 4: To integrate the business logic, you only need to add the annotation MpbFlowControl field to the execution method corresponding to each node in the specific process. The specific parameters include node score, whether it is the final node, role, process definition, etc. .
[0055] Step 5: Since the current code has been sealed, it is not allowed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com