Method, terminal equipment and storage medium for automatically mining business middlemen
An automatic mining and intermediary technology, applied in the field of information processing, can solve problems such as the inability to quickly locate the hierarchical relationship of the industrial chain, difficulty in tracking, and difficulty in meeting the needs of actual combat, so as to reduce the workload of research and judgment and facilitate the analysis of research and judgment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
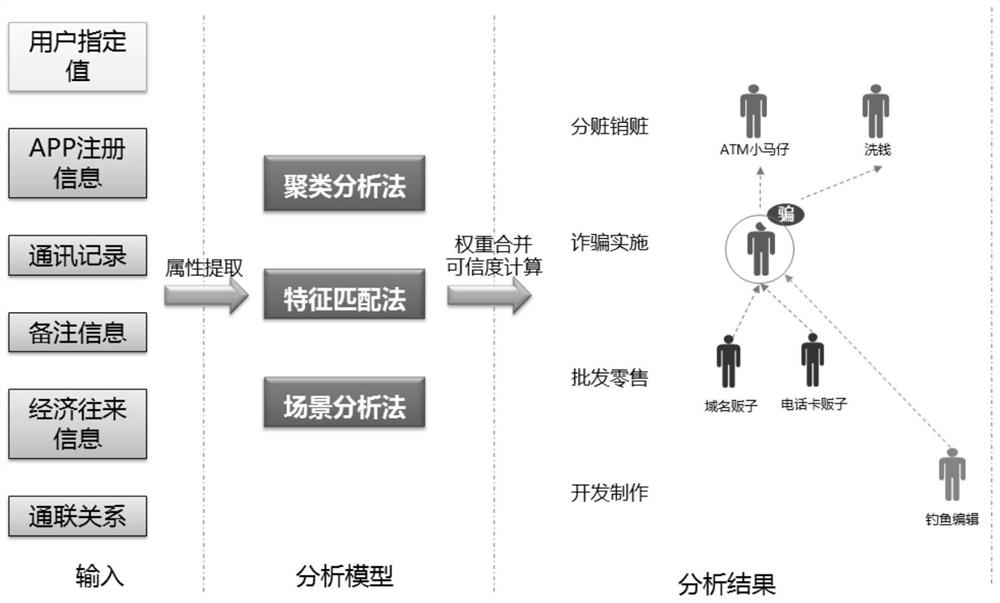
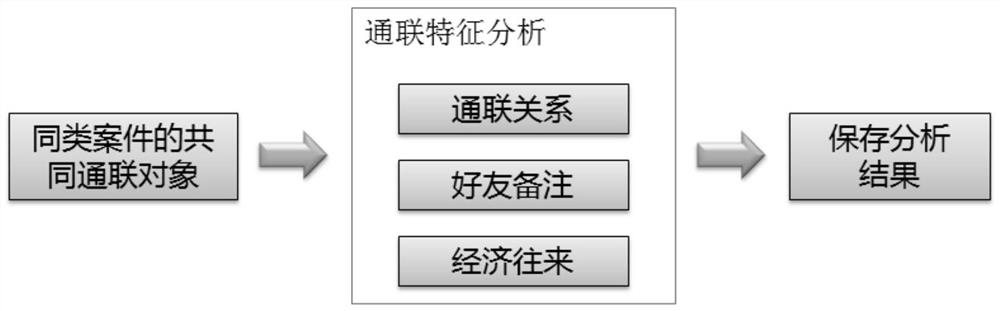
[0039] see Figure 1-Figure 5 As shown, the present invention provides a method for automatically mining business intermediaries,
[0040] The concrete process of the method described in the present invention is as follows:
[0041] S1: Extracting the identity feature attribute of the object to be mined from the mobile phone forensic data: input the mobile phone forensic data, extract at least one identity feature attribute of the object to be mined from the input mobile phone forensic data,
[0042] In addition, a user-specified value can be input, and the user-specified value is an attribute value of an identity characteristic of a known business intermediary associated with the object to be mined, so as to improve the correctness of the analysis result. That is, in order to improve the correctness of identity feature analysis, users are allowed to specify some known attribute values in advance during identity feature analysis. For example, users can manually set a certai...
Embodiment 2
[0067] The present invention also provides a terminal device for automatically mining business intermediaries, including a memory, a processor, and a computer program stored in the memory and operable on the processor. When the processor executes the computer program, the The steps in the above-mentioned method embodiments of the embodiments of the present invention, for example Figure 1-Figure 4 Method steps for steps shown.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com