Data access controlling method crossing safety area based on role mapping
A technology of data access control and role mapping, applied to electrical components, transmission systems, etc., can solve problems that affect the degree of data sharing, cannot function normally, cannot adapt to scale, and achieve the effect of avoiding typical violations of security constraints
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with accompanying drawing.
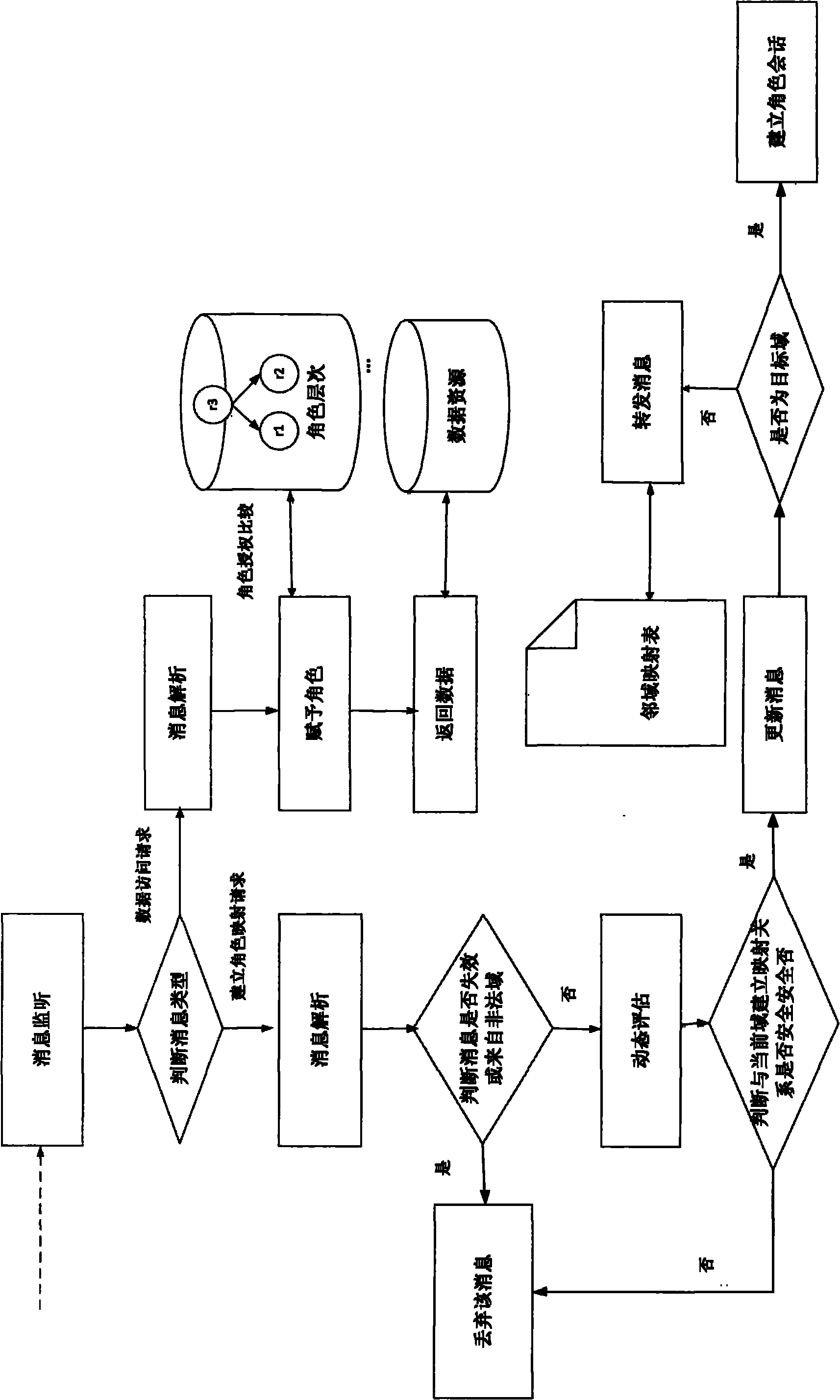
[0037] Such as figure 1 , a method for controlling data access across security domains based on role mapping, the method comprising the following steps:
[0038] (1) Receive and monitor the request message of role mapping, and analyze the role mapping path;
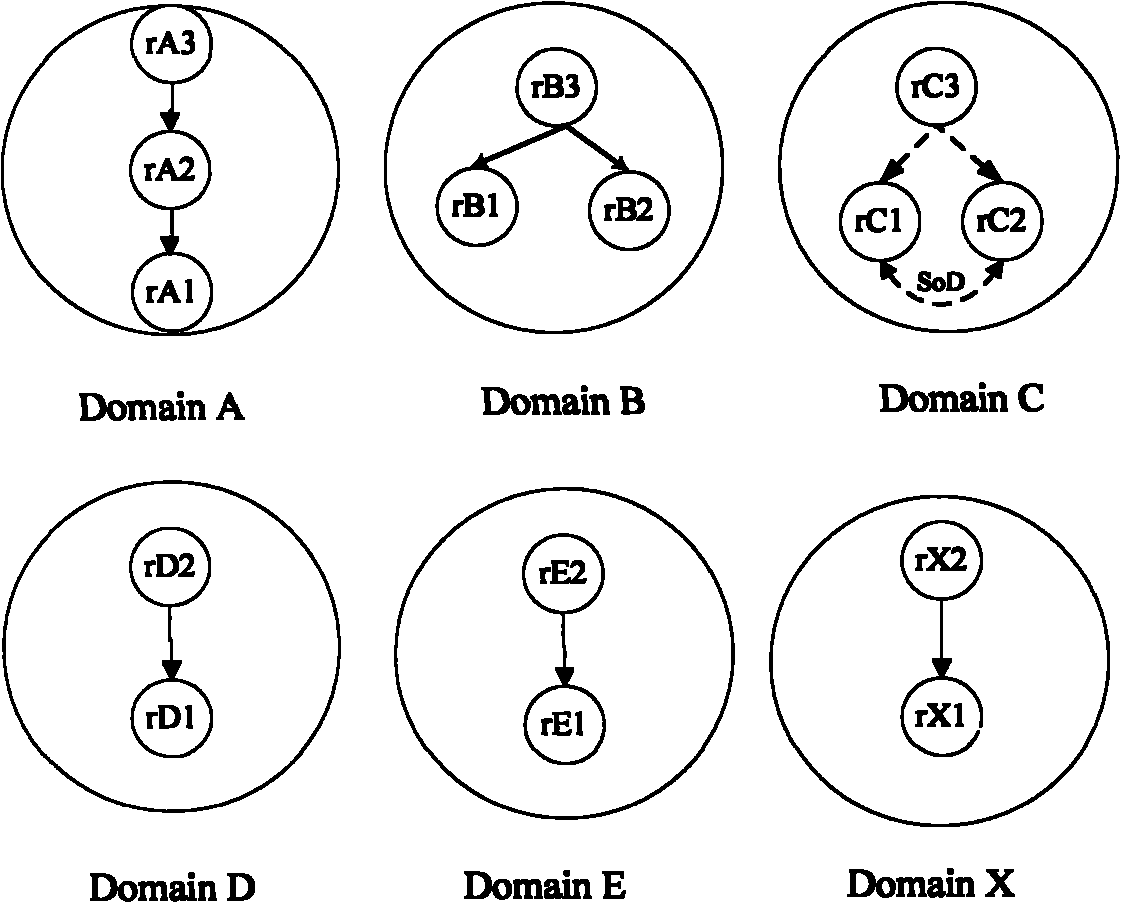
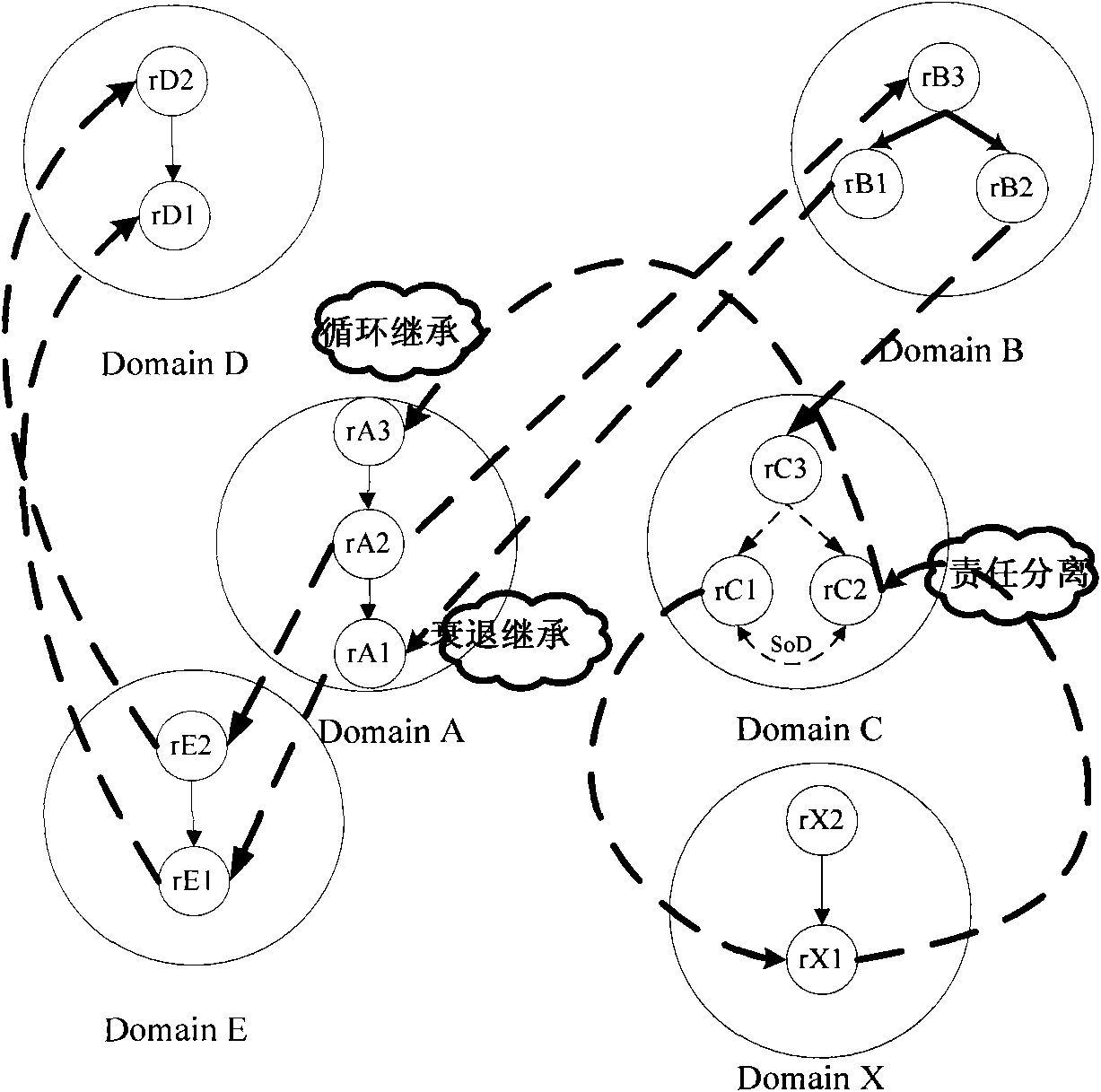
[0039] (2) Judging whether it is safe to establish a mapping with the role of the current domain, and at the same time discover and solve the role decay inheritance;
[0040](3) Forward the request message based on the domain mapping table and the historical path table, discover the target domain and establish a safe role mapping path with it.
[0041] Described step (1) comprises the following steps:
[0042] (1-1) Monitor the request message of the source domain user, and judge the message type;
[0043] (1-2) After the data access request is monitored, the path analysis function Extract including the variable re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com