Method and system for implementing usage monitoring control
A usage monitoring and user technology, applied in transmission systems, digital transmission systems, network traffic/resource management, etc., can solve problems such as policy charging control conflicts, and achieve the effect of avoiding control conflicts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
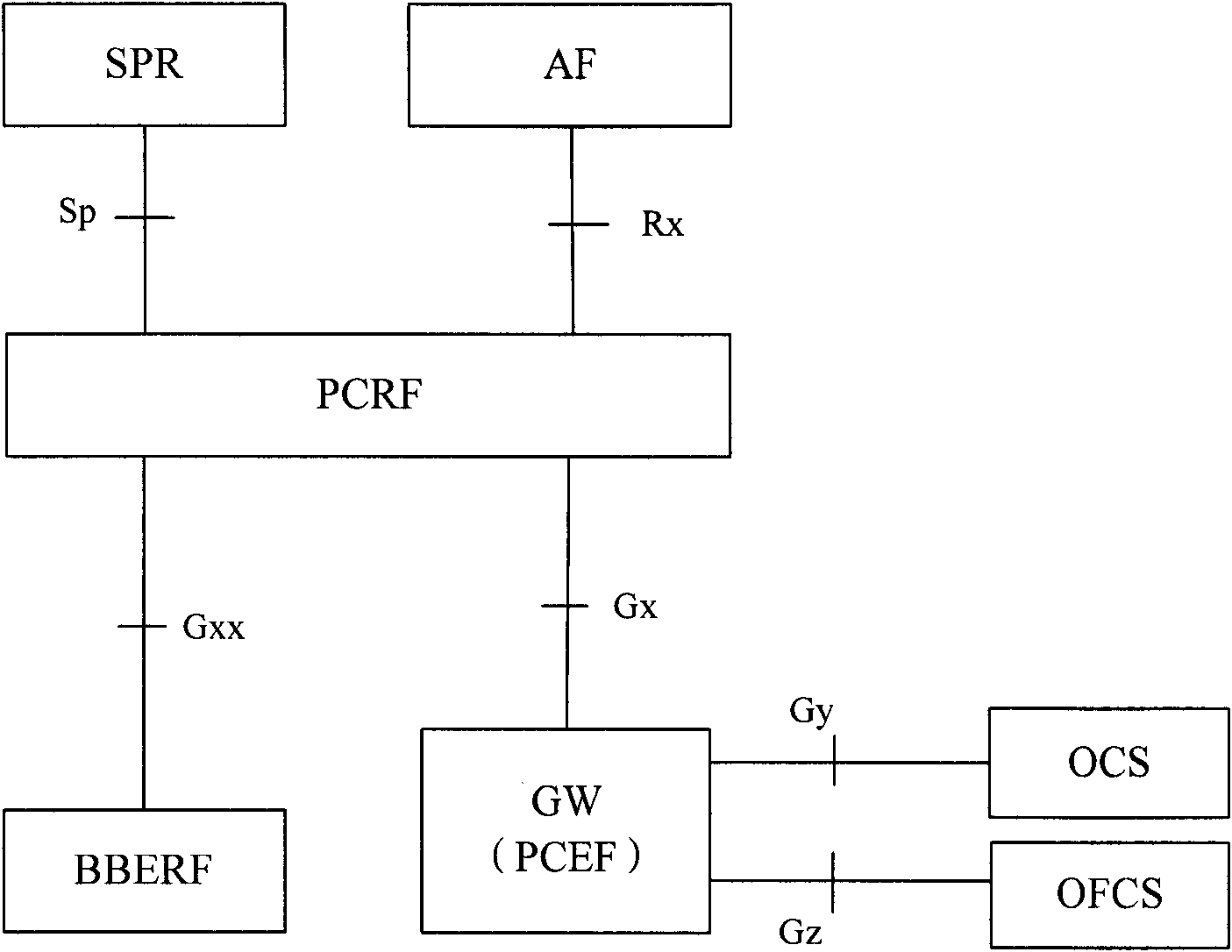
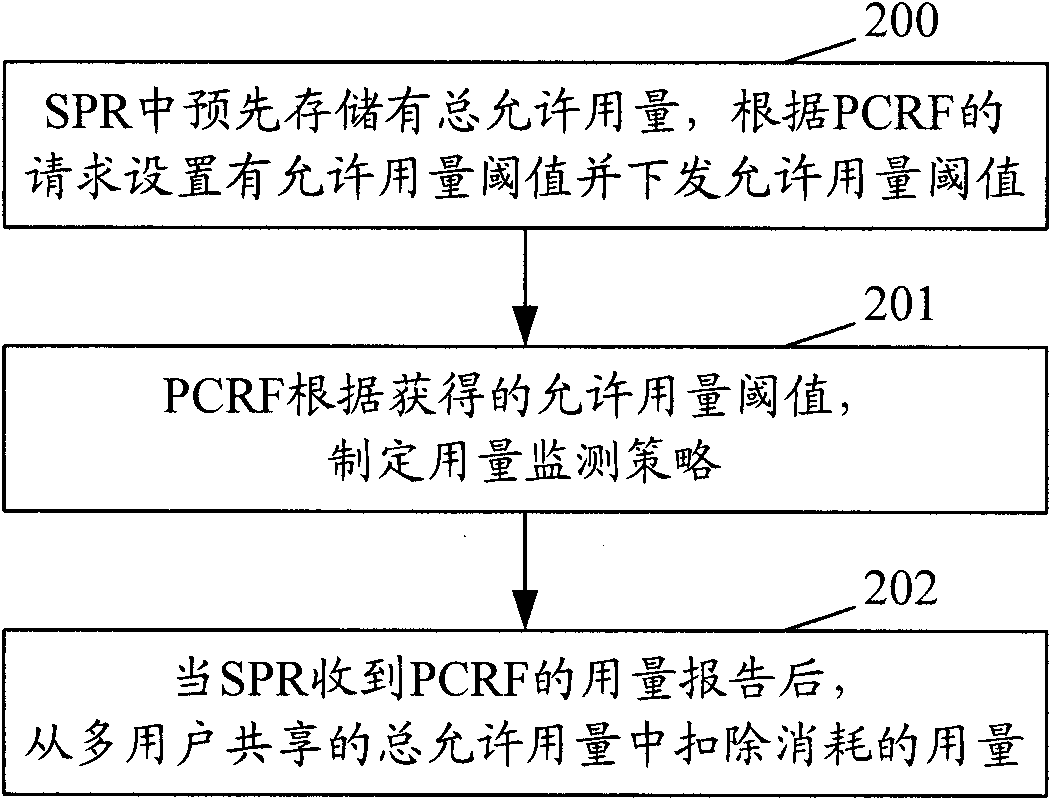
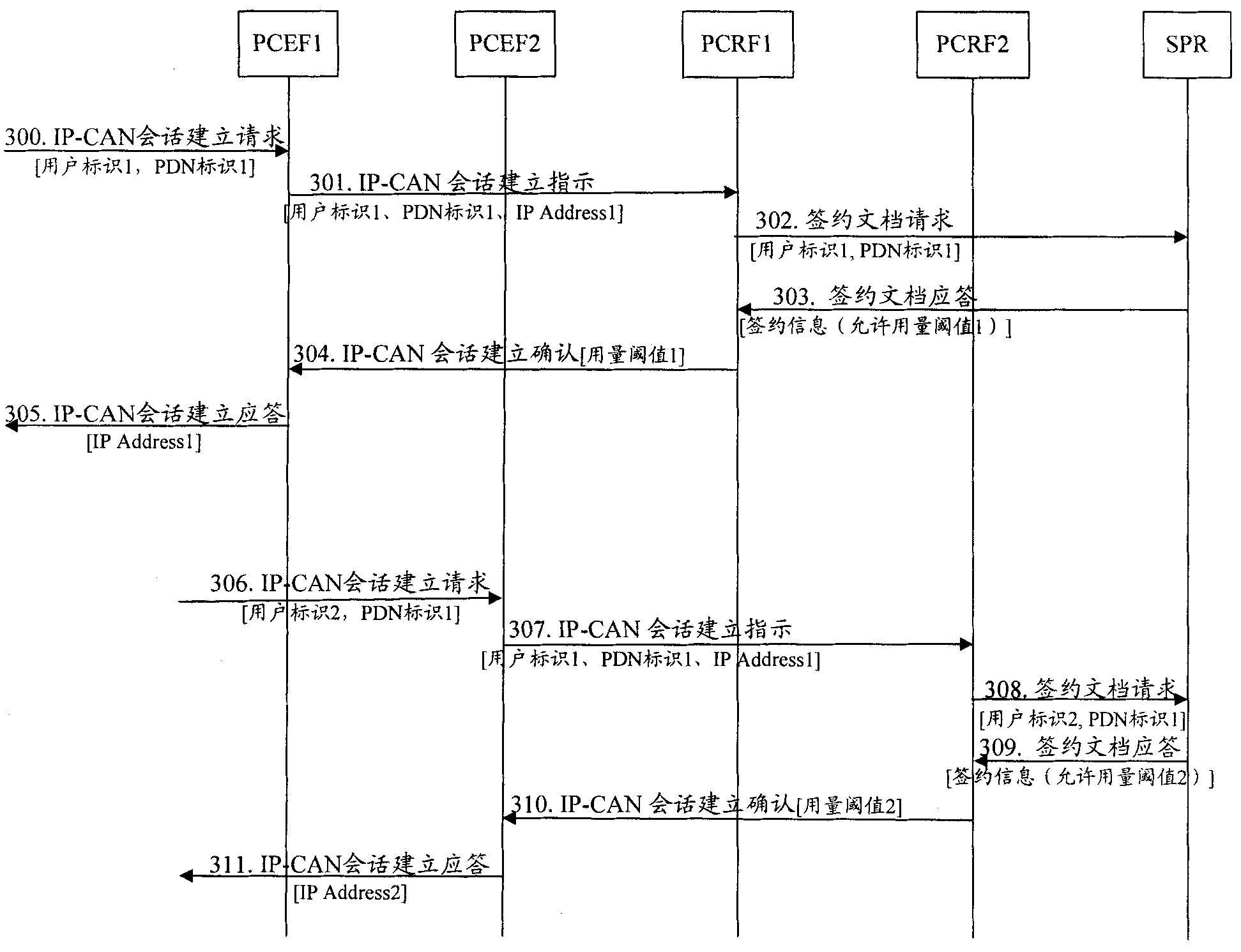
[0058] figure 2 The flow chart of the method that realizes consumption monitoring control for the present invention, as figure 2 shown, including:
[0059] Step 200: The total allowed usage is pre-stored in the SPR, and the allowed usage threshold is set and issued according to the request of the PCRF.
[0060] In this step, assuming that the total allowable usage of the IP-CAN session or service data flow shared by multiple users is TAU, the SPR allocates the allowable usage respectively for the users who initiate the request and share the total allowed usage of the IP-CAN session or service data flow Threshold AUTi, wherein, AUT1
[0061] Step 201: PCRF sets a usage monitoring policy according to the obtained allowed usage threshold. The usage monitoring policy includes the usage threshold assigned by the PCRF to the users corresponding to the IP-CAN sessions or service data flows sharing the total allowed usage.
[0062] In this ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com