Method for managing user purview and judging user operation validity
A technology for managing users and judging permissions, applied in the field of telecommunication network management, can solve the problems of inability to delete permissions, not allowed, etc., to achieve the effect of simple user permissions and convenient operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
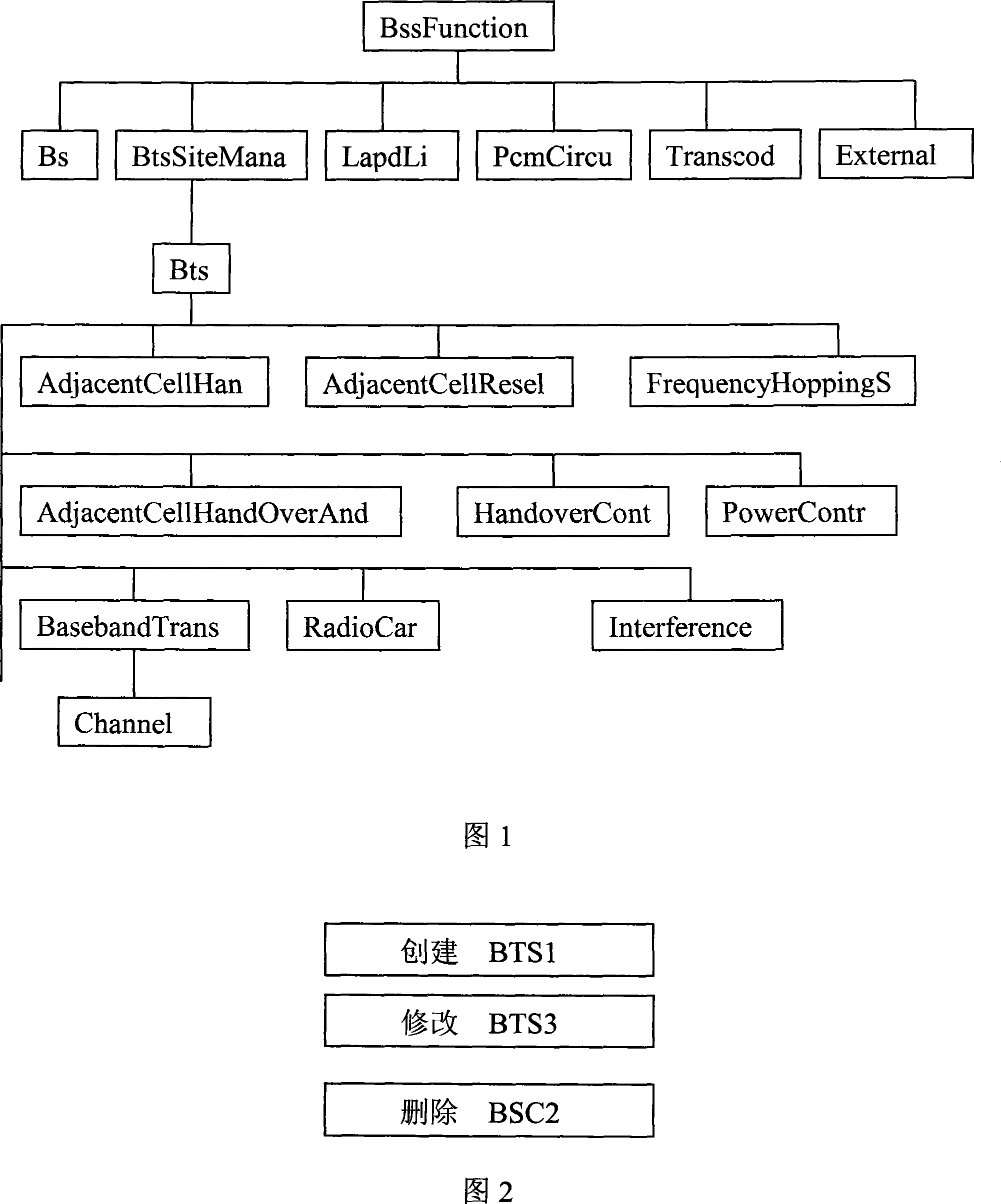
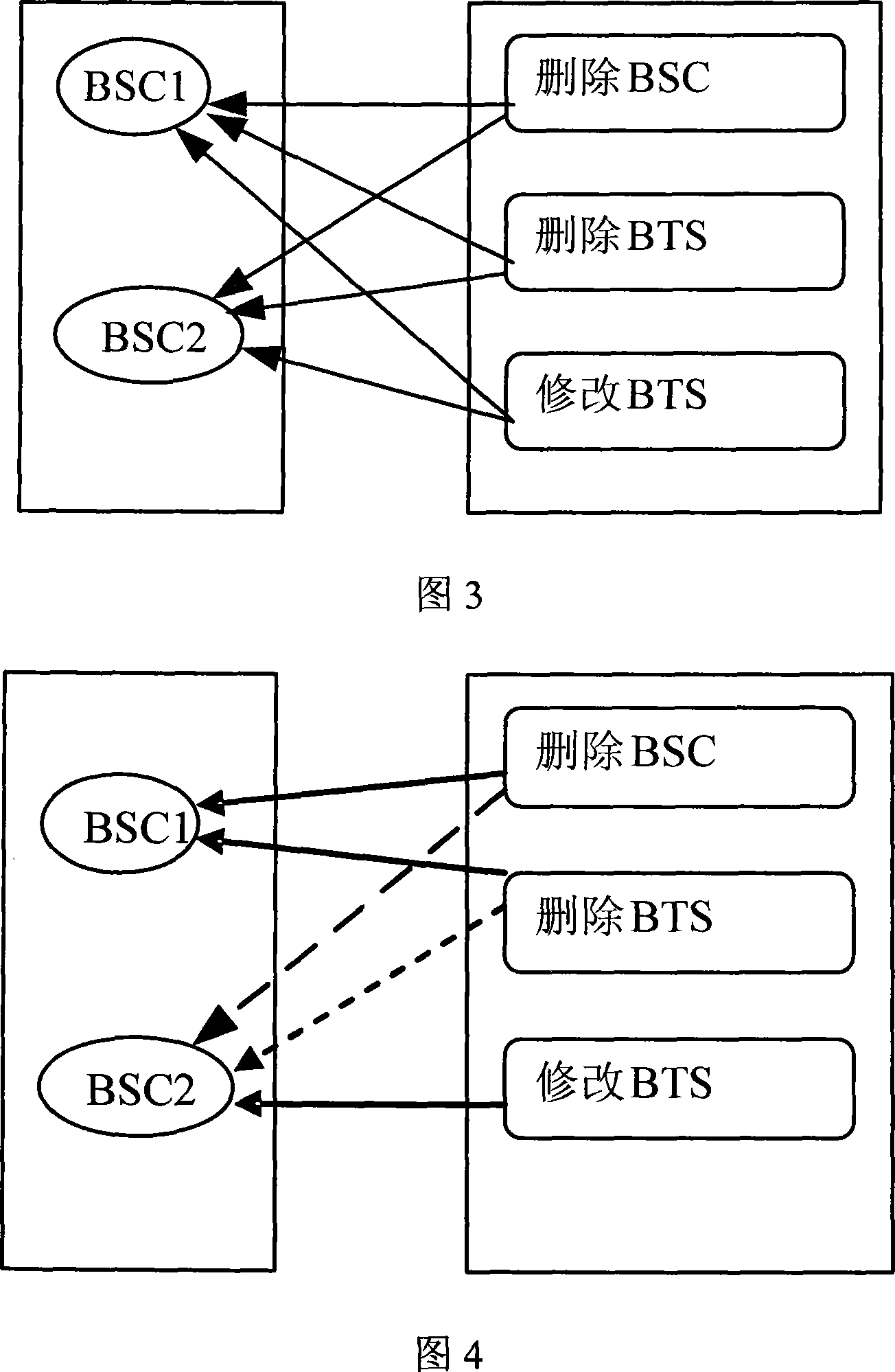
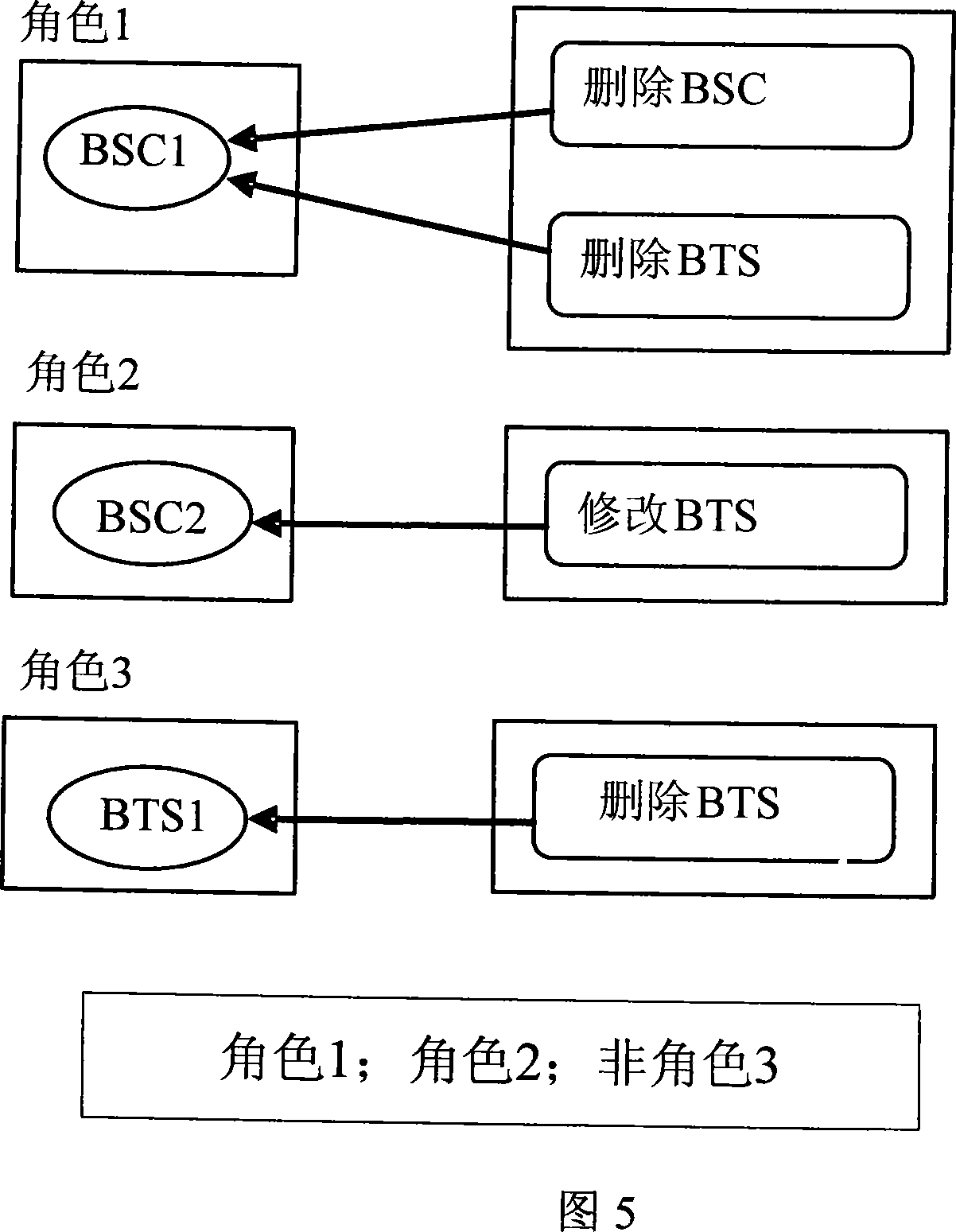
[0035] The present invention provides a method for managing user rights. By adding an intermediate layer in the system, that is, adding a role class, the rights of the role class are object rights plus operation rights; the object rights of a role can include one or more objects Members, the operation authority of a role can also include one or more operation members. Therefore, a role has the various operations contained in its operation permissions for each member in its object permissions and its sub-objects. A user may have the authority of one or more roles, that is, the user's authority is the sum of the authority of one or more roles, and a corresponding relationship between the user authority and the roles it has is established.
[0036] Illustrate the inventive method below in conjunction with accompanying drawing:
[0037] As shown in Figure 5, first define two role classes, the object authority of role 1 is BSC1, and the operation authority is: delete BSC, delete B...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com