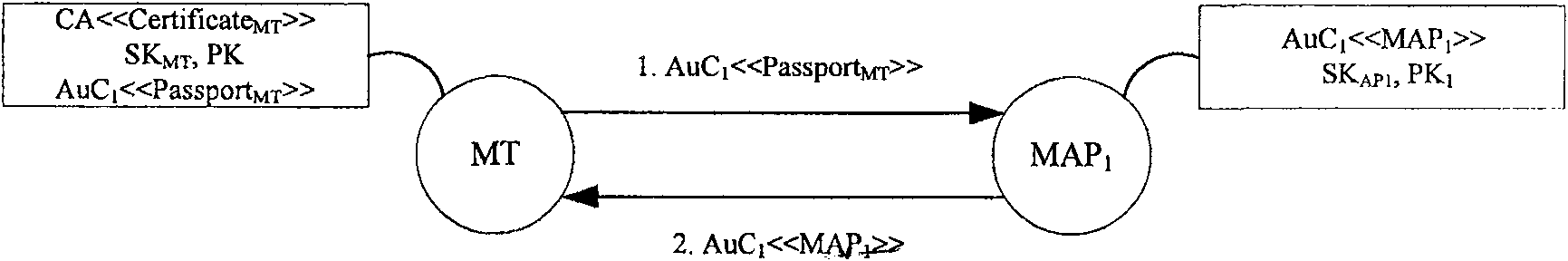Safe and valid instant authentication method in wireless Mesh network
A wireless and network technology, applied in the field of computer networks, can solve problems such as complex algorithms, lack of consideration of full utilization of public key infrastructure resources, and inconvenient implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
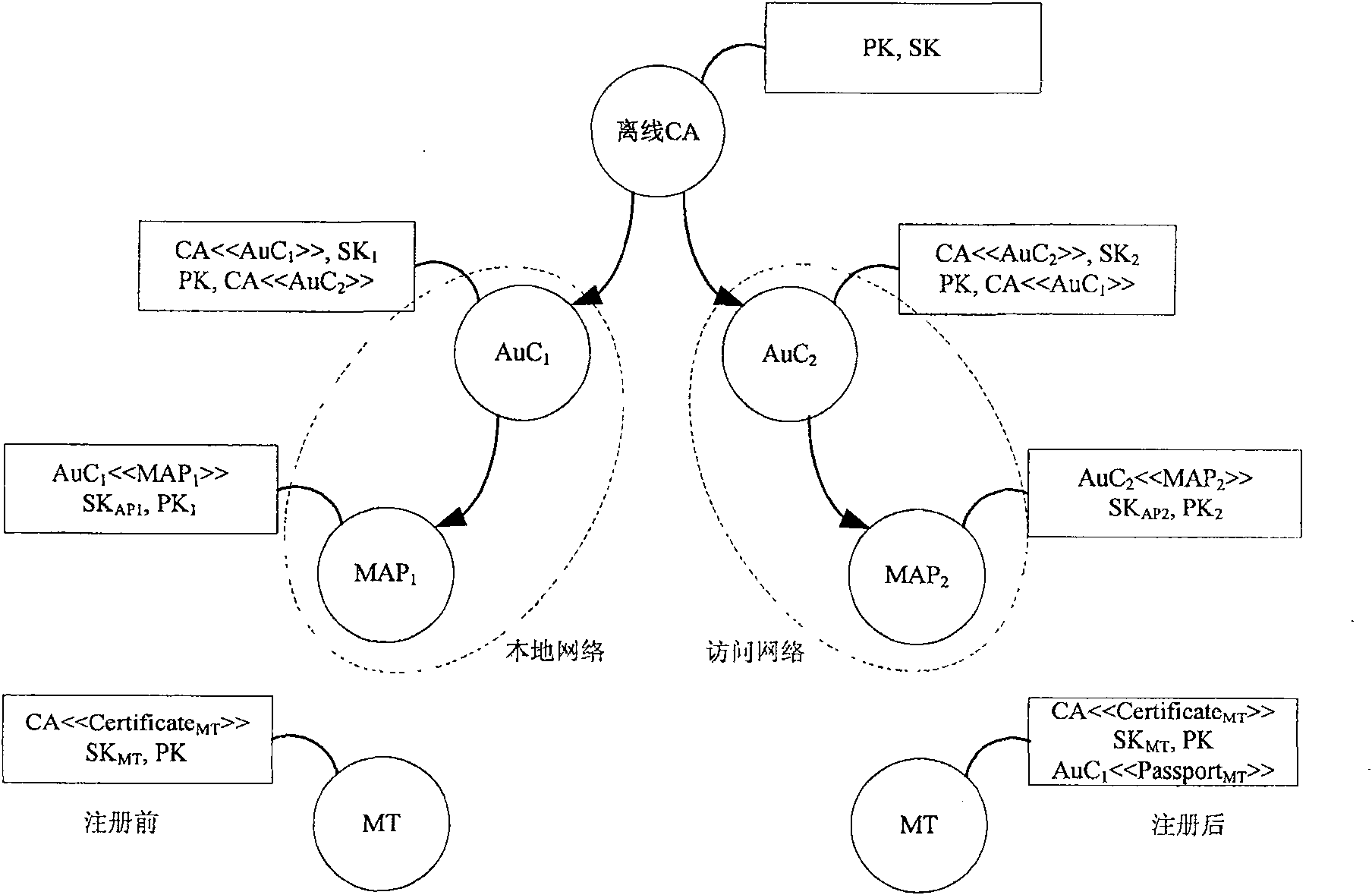
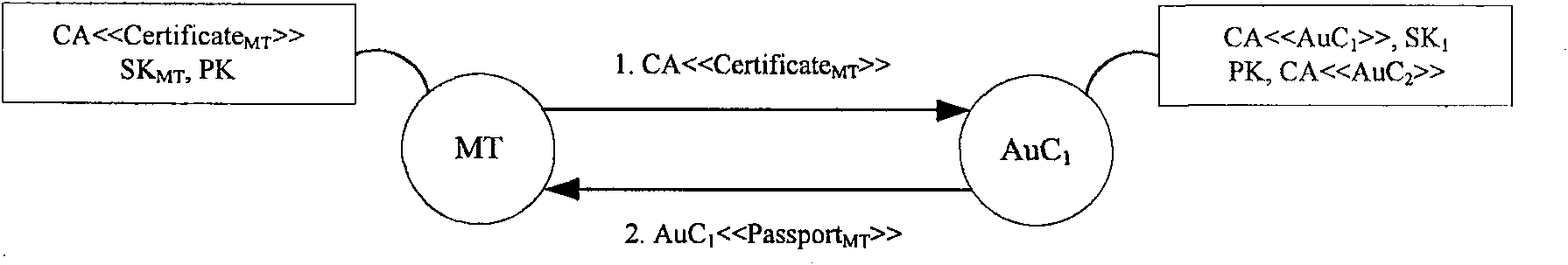
[0113] Specific implementation examples such as Figure 5 As shown, it has the following characteristics:
[0114] The entire wireless mesh network includes a local network H, an access network V and an offline CA that accesses the network only when assigning certificates, updating certificates and publishing change information.
[0115] The local network H includes an authentication center HAuC, a Mesh router HMR and three Mesh access points HMAP 1 、HMAP 2 、HMAP 3 .
[0116]The access network V includes an authentication center VAuC, a mesh router VMR and three mesh access points VMAP 1 、VMAP 2 、VMAP 3 .
[0117] The local network Mesh router HMR is wired to the authentication center HAuC, and the access network Mesh router VMR is wired to the authentication center VAuC.
[0118] Local Network Mesh Access Point HMAP 1 、HMAP 2 、HMAP 3 and access network mesh access point VMAP 1 、VMAP 2 、VMAP 3 Gathered into clusters, they are wirelessly connected at 11Mbps throug...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com